Members of Congress vow to rein in NSA
Yea, sure!!!! The crooks in Congress usually try to convince both sides that they voted to support each side 100 percent!!!!If the House or Senate votes on a single bill several times many members will first vote for the bill, then a second time vote against the same bill. No our Congressmen and Senators are not confused, dyslexic idiots who can't make up their minds. This is very intentional because they want to be able to tell supporters of the bill they voted for the bill, and be able to tell opponents of the bill they voted against the bill.
How they vote on the final bill is usually an indication of which special interest groups gave them the most money.
It's all part of the game plan to get reelected. And to keep us in the dark.
Members of Congress vow to rein in NSA
By Pete Yost Associated Press Wed Jul 17, 2013 10:27 PM
WASHINGTON — In a heated confrontation over domestic spying, members of Congress said Wednesday that they never intended to allow the National Security Agency to build a database of every phone call in America. [If that is true why did they vote for the bill in the first place???] And they threatened to curtail the government’s surveillance authority.
Top Obama administration officials countered that the once-secret program was legal and necessary to keep America safe. And they left open the possibility that they could build similar databases of people’s credit-card transactions, hotel records and Internet searches.
The clash on Capitol Hill undercut President Barack Obama’s assurances that Congress had fully understood the dramatic expansion of government power it authorized repeatedly over the past decade.
The House Judiciary Committee hearing also represented perhaps the most public, substantive congressional debate on surveillance powers since the Sept. 11 terrorist attacks. Previous debates have been largely theoretical and legalistic, with officials in the Bush and Obama administrations keeping the details hidden behind the cloak of classified information.
That changed last month when former government contractor Edward Snowden leaked documents to the Guardian newspaper revealing that the NSA collects every American’s phone records, knowing that the overwhelming majority of people have no ties to terrorism. [Edward Snowden is a patriot and freedom fighter for exposing the lies of Congress, the President and the government] Civil-rights groups have warned for years that the government would use the USA Patriot Act to conduct such wholesale data collection. The government denied it.
The Obama administration says it needs a library of everyone’s phone records so that when it finds a suspected terrorist, it can search its archives for the suspect’s calling habits. The administration says the database was authorized under a provision in the Patriot Act that Congress hurriedly passed after 9/11 and reauthorized in 2005 and 2010. [Well if you ask me the database is NOT allowed by the Fourth Amendment and that should be the final authority on the matter]
The sponsor of that bill, Rep. James Sensenbrenner, R-Wis., said Wednesday that Congress meant only to allow seizures directly relevant to national-security investigations. No one expected the government to obtain every phone record and store them in a huge database to search later. [Bullsh*t, the members of Congress voted for the bill to turn American into a police state, which is what the special interest groups who gave them campaign contributions wanted the bill to do.]
As Deputy Attorney General James Cole explained why that was necessary, Sensenbrenner cut him off and reminded him that his surveillance authority expires in 2015.
“And unless you realize you’ve got a problem,” Sensenbrenner said, “that is not going to be renewed.”
He was followed by Rep. Jerrold Nadler, D-N.Y., who picked up where his colleague left off. The problem, he said, is that the administration considers “everything in the world” relevant to fighting terrorism. [Yea, and so does the House and Senate]
Later, Rep. Blake Farenthold, R-Texas, asked whether the NSA could build similar databases of everyone’s Internet searches, hotel records and credit-card transactions.
Robert S. Litt, general counsel in the office of the Director of National Intelligence, didn’t directly answer, saying it would depend on whether the government believed those records — like phone records — to be relevant to terrorism investigations.
After the phone surveillance became public, Obama assured Americans that Congress was well aware of what was going on. [I suspect Congress was well aware of what was going on, but didn't care, because it served the interests of the special interest groups that give them money]
“When it comes to telephone calls, every member of Congress has been briefed on this program,” he said.
Whether lawmakers willingly kept themselves in the dark or were misled, it was apparent Wednesday that one of the key oversight bodies in Congress remained unclear about the scope of surveillance, more than a decade after it was authorized. [Willingly or not willingly they voted to turn Amerika into a police state and should be booted out of office for that.]
The Judiciary Committee’s senior Democrat, Rep. John Conyers of Michigan, noted that the panel had “primary jurisdiction” over the surveillance laws that were the foundation for the NSA programs. Yet one lawmaker, Rep. Ted Poe, R-Texas, said some members of Congress wouldn’t have known about the NSA surveillance without the sensational leaks: “Snowden, I don’t like him at all, but we would never have known what happened if he hadn’t told us.” [Again bullsh*t. That's like saying a drunk drive didn't know he was drunk because nobody told him he was weaving all over the road]
The NSA says it looks at numbers only as part of narrow terrorism investigations, but that doesn’t tell the whole story. [Narrow terrorism investigations??? What rubbish. I think NSA has been collecting phone call data on 100+ million people or roughly a third of the American population.]
For the first time, NSA Deputy Director John C. Inglis disclosed Wednesday that the agency sometimes conducts what’s known as three-hop analysis. That means the government can look at the phone data of a terrorism suspect, plus the data of all of his contacts, then all of those people’s contacts, and finally, all of those people’s contacts.
If the average person calls 40 unique people, three-hop analysis could allow the government to mine the records of 2.5 million Americans when investigating one terrorism suspect. [Well I guess using that definition NSA's spying on 100+ million people's phone records it is a narrow investigation]
Rep. Randy Forbes, R-Va., said such a huge database was ripe for government abuse. When Inglis said there was no evidence of that, Forbes interrupted:
“I said I wasn’t going to yell at you and I’m going to try not to. That’s exactly what the American people are worried about,” he said. “That’s what’s infuriating the American people. They’re understanding that if you collect that amount of data, people can get access to it in ways that can harm them.”
The government says it stores everybody’s phone records for five years. Cole explained that because the phone companies don’t keep records that long, the NSA had to build its own database. [Since when is it the job of the phone companies to spy on people for NSA???]
Rep. Steve King, R-Iowa, asked why the government didn’t simply ask the phone companies to keep their data longer. [I guess if Rep. Steve King has his way he will pass a law making it the phone companies job to spy on people for Congress!!!] That way, the government could ask for specific information, rather than collecting information on millions of innocent people.
Inglis said it would be challenging, but the government was looking into it.
Near the end of the hearing, Litt struck a compromising tone. He said national-security officials had tried to balance privacy and security. [Bullsh*t!!!!]
“If the people in Congress decide that we’ve struck that balance in the wrong place, that’s a discussion we need to have,” he said. [Well Congress is the gang of criminals that decided to flush the Bill of Rights down the toilet by passing the Patriot Act]
Obama, too, has said he welcomes the debate over surveillance. But his administration never wanted the debate to be quite so specific. [Obama would prefer that we don't know that he is spying on us]
That was obvious when Rep. Bob Goodlatte, R-Va., asked Litt whether he really believed the government could keep such a vast surveillance program a secret forever.
“Well,” Litt replied, “we tried.” [And thanks to patriot and freedom fighter Edward Snowden the American public found out]
ACLU: Nearly all drivers tracked by police
I certainly agree with the police and our government masters that if the police spy on us 24/7 it will make it easier for the cops to catch nasty, evil criminals.Of course I think most Americans including my self think it is a waste of our tax dollars to have the government spy on millions of honest, law abiding Americans just to catch a few criminals.
I certainly don't want to pay hundreds or thousands of dollars a year in taxes to allow pay some cop to spy on me 24/7 and build up a huge dossier to be used against me, just in case the police suspect that I committed a crime.
I also think it is an invasion of my privacy for some jackbooted police thug to spy on me 24/7, just in case I turn out to be a criminal.
Last but not least I also think it is a violation of my 4th and 5th Amendment rights for the government to have the cops following me around 24/7 spying on me, just in case I turn out to be a terrorist.
And I suspect the Founders agree with me, and that is probably what they passed the Bill of Rights to limit the power of the police and government.
ACLU: Nearly all drivers tracked by police
By Anne Flaherty and Calvin Woodward Associated Press Wed Jul 17, 2013 10:28 PM
WASHINGTON — You can drive, but you can’t hide.
A rapidly growing network of police cameras is capturing, storing and sharing data on license plates, making it possible to stitch together people’s movements, whether they are stuck in a commute, making tracks to the beach or up to no good.
For the first time, the number of license-tag captures has reached the millions, according to a study published Wednesday by the American Civil Liberties Union based on information from hundreds of law-enforcement agencies. Departments keep the records for weeks or years, sometimes indefinitely, saying they can be crucial in tracking suspicious cars, aiding drug busts, finding abducted children and more.
Attached to police cars, bridges or buildings — and sometimes merely as an app on a police officer’s smartphone — scanners capture images of passing or parked vehicles and pinpoint their locations, uploading that information into police databases.
Over time, it’s unlikely many vehicles in a covered area escape notice. And with some of the information going into regional databases encompassing multiple jurisdictions, it’s becoming easier to build a record of where someone has been, and when, over a large area.
Law-enforcement agencies in the Valley have used the scanners for years and typically tout them as a way to identify stolen vehicles.
Mesa was the first agency to buy in to the technology, with a $25,000 system the agency purchased in 2005. Police in communities including Peoria, Chandler and Phoenix, as well as the Arizona Department of Public Safety, followed.
Between September 2005 and February 2008, Mesa police used the technology to recover more than $2 million in stolen vehicles. [I guess that is typical police propaganda. Giving us dollar value of vehicles recovered instead of an actual number to make things sound better. If the cops assume a new car costs $50,000 that means the cops only recovered a lousy 40 cars. On the other hand cops tend to over inflate their numbers so maybe they used a value of $100,000 per car recovered meaning they only recovered a stinking 20 cars. When I was a kid and the cops busted somebody with a kilo of marijuana that cost $100, they would inflate the value to $1,600 by saying that kilo could be split into 40 ounce bags which sold for $10 each, giving the kilo a value of $400. Then they would say each ounce bag of weed could be rolled into 40 marijuana cigarettes which could be sold for $1 each inflating a $10 bag of weed to be worth $40, and inflating the value of the $100 kilo to $1,600. I suspect the cops play the same silly games to inflate the value of the stolen vehicles recovered to make themselves look like superhuman heroes.]
The ACLU filed requests with Phoenix, Chandler and the Pinal County Sheriff’s Office, according to documents available on the group’s site.
Chandler police responded to the ACLU’s request about access to the license-plate records with a statement that read, in part, “Members of the auto theft unit are currently the only departmental members who have access to the database.” [Yea, sure!!!! But I suspect the members of the auto theft unit with share their information with any other cop who claims he needs it for any reason to catch bad guys]
Phoenix police retain information on the scanned plates for three years and investigators must go through the auto-theft detail to access the records. There are about 1.9 million plate reads in the system, which include partial plates and duplicates, according to a police spokesman.
Unauthorized access to the records could lead to discipline for a violation of office policy or to criminal charges. [Give me a break. Sure on paper this COULD happen, but I doubt if any cop ever gets punished for breaking the rules. And if they get punished it is rarely more then a slap on the wrist]
While the Supreme Court ruled in 2012 that a judge’s approval is needed to use GPS to track a car, networks of plate scanners allow police effectively to track a driver’s location, sometimes several times every day, with few legal restrictions. The ACLU says the scanners are assembling a “single, high-resolution image of our lives.”
“There’s just a fundamental question of whether we’re going to live in a society where these dragnet surveillance systems become routine,” said Catherine Crump, a staff attorney with the organization. The group is proposing that police departments immediately delete records of cars not linked to any crime. [An even better idea would be to not allow the cops to collect this data!!!!]
Although less thorough than GPS tracking, plate readers can produce some of the same information, the group says, revealing whether someone is frequenting a bar, joining a protest, getting medical or mental help, being unfaithful to a spouse and much more.
In Minneapolis, for example, eight mobile and two fixed cameras captured data on 4.9 million license plates from January to August 2012, the Star Tribune reported. Among those whose movements were recorded: Mayor R.T. Rybak, whose city-owned cars were tracked at 41 locations in a year.
A Star Tribune reporter’s vehicle was tracked seven times in a year, placing him at a friend’s house three times late at night, other times going to and from work — forming a picture of the dates, times and coordinates of his daily routine. Until the city temporarily classified such data late last year, anyone could ask police for a list of when and where a car had been spotted.
As the technology becomes cheaper and more widespread, even small police agencies deploy more sophisticated systems. The federal government has been a willing partner, offering grants to help equip departments, in part as a tool against terrorism.
Law-enforcement officials say the scanners are strikingly efficient. The state of Maryland told the ACLU that troopers could “maintain a normal patrol stance” while capturing up to 7,000 license plate images in a single eight-hour shift.
“At a time of fiscal and budget constraints, we need better assistance for law enforcement,” said Harvey Eisenberg, assistant U.S. attorney in Maryland. [Well if they want to save money, they could stop these surveillance programs which are just jobs programs for cops]
Law-enforcement officials say the technology automates a practice that’s been around for years. The ACLU found that only five states have laws governing license-plate readers. New Hampshire, for example, bans the technology except in narrow circumstances, while Maine and Arkansas limit how long plate information can be stored.
“There’s no expectation of privacy” for a vehicle driving on a public road or parked in a public place, said Lt. Bill Hedgpeth, a spokesman for the Mesquite Police Department in Texas. The department has records stretching back to 2008, although the city plans next month to begin deleting files older than two years.
In Yonkers, N.Y., just north of New York City’s Bronx, police said retaining the information indefinitely will help detectives solve future crimes. In a statement, the department said it uses license-plate readers as a “reactive investigative tool” that is accessed only if detectives are looking for a particular vehicle in connection with a crime. [Translation - if we think you are a criminal we will use any and all of the data we collect against you]
“These plate readers are not intended nor used to follow the movements of members of the public,” the department said. [What bullsh*t!!! That's the whole purpose of the data - spying on the entire public to find a small number of criminals]
Even so, the records add up quickly. In Jersey City, N.J., for example, the population is 250,000, but the city collected more than 2 million plate images in a year. Because the city keeps records for five years, the ACLU estimates that it has 10 million on file, making it possible for police to plot the movements of most residents, depending upon the number and location of the scanners.
The ACLU study, based on 26,000 pages of responses from 293 police departments and state agencies across the country, found that license-plate scanners produced a small fraction of “hits,” or alerts to police that a suspicious vehicle had been found.
In Maryland, for example, the state reported reading about 29 million plates between January and May of last year. Of that number, about 60,000 — or roughly 1 in every 500 license plates — were suspicious. The main offenses: a suspended or revoked registration, or a violation of the state’s emissions- inspection program, altogether accounting for 97 percent of alerts. [Sounds like most of those are TAX violations - the government wants to spy on us 24/7 to make it easier to shake us down for vehicle registration taxes]
Even so, Eisenberg, the assistant U.S. attorney, said the program has helped authorities track 132 wanted suspects and can make a critical difference in keeping an area safe.
Also, he said, Maryland has rules in place restricting access. Most records are retained for one year, and the state’s privacy policies are reviewed by an independent board, Eisenberg said.
At least in Maryland, “there are checks, and there are balances,” he said.
Republic reporter JJ Hensley contributed to this article.
Frequently when one bill is heard several times in either the House or Senate a Congressman or Senator will vote for the bill one time, and then against the bill the second time.
No the these folks are not dyslexic nut jobs who don't know what is going on. They intentionally vote BOTH ways, so they can tell supporters of the bill they voted for the bill and tell opponents of the bill that they voted against the bill.
Of course their final vote for the bill will almost always represent the voice of what ever special interest group gave them the most cold hard cash in campaign contributions.
Letter: Congress should try listening to constituents before voting
Posted: Thursday, July 18, 2013 12:16 pm
Letter to the Editor
Congressman Matt Salmon claims to be concerned with “the erosion of our constitutional rights,” according to a recent press release on his sponsorship of the LIBERT-E Act. While he appears to have a legitimate concern for constitutional rights and liberties, his voting record begs to differ.
Let’s go back to the beginning of 2013. In February, CISPA was reintroduced to the House. This bill raised heavy criticism from both sides of the aisle as to the Internet surveillance powers it granted to the federal government. The bill passed with support from Congressman Salmon. Then, last month, the NSA leaks hit the press and government surveillance became the most discussed issue of the summer.
Kicking off the anti-NSA tirade was a congressional letter to Keith Alexander demanding answers to questions on how the FBI and the NSA collect internet information and cellular metadata. Among the 25 signatures on this letter was Rep. Salmon’s. Why is this Representative who voted to extend Patriot Act surveillance powers to the federal government suddenly interested in their use? After a call to his local office, a spokesperson claimed that he “regrets” voting in favor of CISPA. Congressmen don’t get to just regret a controversial vote.
Is Salmon’s sponsorship of the LIBERT-E Act a sincere effort to limit unconstitutional federal surveillance, or is it merely an appeal to the now-outraged conservative voting population he represents? Maybe the next time he votes he should listen to his constituent concerns rather than ignoring them until it becomes an unpopular practice.
Andrew Barber
Gilbert
The process is identical to using "denial of service attacks" to knock out an internet web site. Just have a whole bunch of phones at the same time call the land line number you want to shut down.
Many years ago I read a story about a couple who where ripped off by a national tele-Evangelical preacher who conned them into donating their life savings to his phoney baloney religion.
The couple's son got even with the preacher by having his computer dial the preachers 800 number continuously to prevent other people from calling it.
Just for fun I bought a few chips at Radio Shack and built a circuit board for a few bucks to do the same thing. Now I guess you wouldn't even have to build your own hardware to do it but could buy a board with a PIC chip on it and program it to continuously dial the same number. Total cost under $50. For that matter I suspect you could write an application on these new "smart" cell phones to do the same thing.
VoIP phone hackers pose public safety threat
By Paresh Dave
July 18, 2013, 7:15 p.m.
The demand stunned the hospital employee. She had picked up the emergency room's phone line, expecting to hear a dispatcher or a doctor. But instead, an unfamiliar male greeted her by name and then threatened to paralyze the hospital's phone service if she didn't pay him hundreds of dollars.
Shortly after the worker hung up on the caller, the ER's six phone lines went dead. For nearly two days in March, ambulances and patients' families calling the San Diego hospital heard nothing but busy signals.
The hospital had become a victim of an extortionist who, probably using not much more than a laptop and cheap software, had single-handedly generated enough calls to tie up the lines.
Distributed denial-of-service attacks — taking a website down by forcing thousands of compromised personal computers to simultaneously visit and overwhelm it — has been a favored choice of hackers since the advent of the Internet.
Now, scammers are inundating phone lines by exploiting vulnerabilities in the burgeoning VoIP, or Voice over Internet Protocol, telephone system.
The frequency of such attacks is alarming security experts and law enforcement officials, who say that while the tactic has mainly been the tool of scammers, it could easily be adopted by malicious hackers and terrorists to knock out crucial infrastructure such as hospitals and 911 call centers.
"I haven't seen this escalated to national security level yet, but it could if an attack happens during a major disaster or someone expires due to an attack," said Frank Artes, chief technology architect at information security firm NSS Labs and a cybercrime advisor for federal agencies.
The U.S. Department of Homeland Security declined to talk about the attacks but said in a statement that the department was working with "private and public sector partners to develop effective mitigation and security responses."
In the traditional phone system, carriers such as AT&T grant phone numbers to customers, creating a layer of accountability that can be traced. On the Web, a phone number isn't always attached to someone. That's allowed scammers to place unlimited anonymous calls to any land line or VoIP number.
They create a personal virtual phone network, typically either through hardware that splits up a land line or software that generates online numbers instantly. Some even infect cellphones of unsuspecting consumers with viruses, turning them into robo-dialers without the owners knowing that their devices have been hijacked. In all cases, a scammer has access to multiple U.S. numbers and can tell a computer to use them to dial a specific business.
Authorities say the line-flooding extortion scheme started in 2010 as phone scammers sought to improve on an old trick in which they pretend to be debt collectors. But the emerging bulls-eye on hospitals and other public safety lines has intensified efforts to track down the callers.
Since mid-February, the Internet Crime Complaint Center, a task force that includes the FBI, has received more than 100 reports about telephony denial-of-service attacks. Victims have paid $500 to $5,000 to bring an end to the attacks, often agreeing to transfer funds from their banks to the attackers' prepaid debit card accounts. The attackers then use the debit cards to withdraw cash from an ATM.
The hospital attack, confirmed by two independent sources familiar with it, was eventually stopped using a computer firewall filter. No one died, the sources said. But hospital staff found the lack of reliable phone service disturbing and frustrating, one source said. They requested anonymity because they were not authorized to talk about the incident.
But typical firewalls, which are designed to block calls from specific telephone numbers, are less effective against Internet calls because hackers can delete numbers and create new ones constantly. Phone traffic carried over the Internet surged 25% last year and now accounts for more than a third of all international voice traffic, according to market research firm TeleGeography.
To thwart phone-based attacks, federal officials recently began working with telecommunications companies to develop a caller identification system for the Web. Their efforts could quell more than just denial-of-service attacks.
They could block other thriving fraud, including the spoofing and swatting calls that have targeted many people, from senior citizens to celebrities such as Justin Bieber. In spoofing, a caller tricks people into picking up the phone when their caller ID shows a familiar number. In swatting, a caller manipulates the caller ID to appear as though a 911 call is coming from a celebrity's home.
Unclassified law enforcement documents posted online have vaguely identified some victims: a nursing home in Marquette, Wis., last November, a public safety agency and a manufacturer in Massachusetts in early 2013, a Louisiana emergency operations center in March, a Massachusetts medical center in April and a Boston hospital in May.
Wall Street firms, schools, media giants, insurance companies and customer service call centers have also temporarily lost phone service because of the attacks, according to telecommunications industry officials. Many of the victims want to remain anonymous out of fear of being attacked again or opening themselves up to lawsuits from customers.
The Marquette incident is noteworthy because when the business owner involved the Marquette County Sheriff's Department, the scammer bombarded one of the county's two 911 lines for 3 1/2 hours.
"The few people I've talked to about it have said that you just have to take it and that there's no way to stop this," Sheriff's Capt. Chris Kuhl said.
A Texas hospital network has been targeted several times this year, said its chief technology officer, who spoke on the condition of anonymity because the individual's employer has not discussed the attacks publicly. One of its nine hospitals lost phone service in a nurses unit for a day, preventing families from calling in to check on patients.
As the hospital searched for answers, it temporarily created a new number and turned to backup phone lines or cellphones for crucial communications. The chain eventually spent $20,000 per hospital to install a firewall-type device that is able to block calls from numbers associated with an attack.
For all the money spent on Internet security, companies often overlook protecting their telephones, Artes said.
"It's kind of embarrassing when a website goes down, but when you shut down emergency operations for a county or a city, that has a direct effect on their ability to respond," he said.
The Federal Communications Commission has begun huddling with phone carriers, equipment makers and other telecommunication firms to discuss ideas that would help stem the attacks. One possibility is attaching certificates, or a secret signature, to calls.
The FCC's chief technology officer, Henning Schulzrinne, acknowledged that though such a solution is probably a year or two away, it could put an end to most fraudulent calls.
But Jon Peterson, a consultant with network analytics firm Neustar, said such measures raise privacy worries. Some calls, such as one to a whistle-blower hotline or one originating from a homeless shelter, may need to remain anonymous. There won't be a single fix. But the goal is clear.
"The lack of secure attribution of origins of these calls is one of the key enablers of this attack," Peterson said. "We have to resolve this question of accountability for the present day and the future."
paresh.dave@latimes.com
Twitter: @peard33
“No one buys a cell phone to share detailed information about their whereabouts with the police. That was true in 2006 and is equally true today. Citizens have a legitimate privacy interest in such information.”
N.J. court: Warrants needed for cellphone tracking
By David Porter Associated Press Fri Jul 19, 2013 6:19 AM
NEWARK, N.J. — Police in New Jersey will soon have to get warrants if they want to track suspects using cellphone data, the state’s Supreme Court ruled in a decision that affords citizens here more privacy protections than they enjoy under federal law.
In a unanimous ruling Thursday stemming from the arrest of a burglary suspect in 2006, the court directed that beginning in 30 days, all law enforcement officers must get a search warrant based on probable cause if they want to get access to cellphone locating data. Since 2010, police have had to satisfy a lower standard of demonstrating there are “reasonable grounds” to believe the information would be relevant to an investigation.
“No one buys a cell phone to share detailed information about their whereabouts with the police,” Chief Justice Stuart Rabner wrote. “That was true in 2006 and is equally true today. Citizens have a legitimate privacy interest in such information.”
Rabner noted that federal courts have been divided over the issue of cellphone tracking by law enforcement. In some other areas, he wrote, New Jersey’s constitution goes farther than the Fourth Amendment in protecting citizens from unreasonable search and seizure — particularly in previous cases involving Internet usage, bank records and hotel telephone records.
“When people make disclosures to phone companies and other providers to use their services, they are not promoting the release of personal information to others. Instead, they can reasonably expect that their personal information will remain private,” Rabner wrote. “For those reasons, we have departed from federal case law that takes a different approach.”
Rubin Sinins, an attorney who argued on behalf of the American Civil Liberties Union of New Jersey and a state criminal defense lawyers association, called Thursday’s decision “vitally important.”
“I’m not surprised it was unanimous because the basic premise of the opinion is quite logical and consistent with citizens’ reasonable expectation of privacy in their cellphone usage,” he said.
In the 2006 case, police tracked Robert Earls to a motel on Route 9 in Howell using information provided by T-Mobile about the location of a cellphone believed to be in his possession. When he opened the door to his room, police saw items they believed had been stolen and arrested him. He eventually pleaded guilty to burglary and theft.
It wasn’t immediately clear how Earls’ case would be affected by the ruling since a lower court will now have to consider whether police were justified in using the cellphone data without a warrant under an exception for emergency circumstances. Police said they believed Earls’ girlfriend was in danger because she had cooperated with them.
The new warrant rule applies only to Earls’ case and future cases. The state attorney general’s office has trained county law enforcement personnel to obtain warrants for GPS-based location data since 2006, and warrants were obtained in about 85 percent of 600 cases involving cellphone location data for a six-month period last year, according to Thursday’s ruling.
“As a practical matter, this ruling only affects future cases, and police in New Jersey already have been routinely seeking probable-cause based warrants before seeking cellphone location information,” attorney general’s office spokesman Peter Aseltine said in an email. “We will implement training for New Jersey law enforcement to ensure compliance with this ruling.”
NSA director suggests phone companies, not government, could store calling records
By Robert O’Harrow Jr., Published: July 18 E-mail the writer
ASPEN, Colo. — The director of the National Security Agency said Thursday that he is open to the idea of allowing telephone companies, rather than the NSA, to store vast pools of calling records that could be used in counterterrorism cases.
Speaking at a security conference, Gen. Keith Alexander strongly defended the spy agency’s surveillance efforts, which rely on the information known as calling “metadata” to identify and track terrorists and their plots.
Congress should try listening to constituents before voting
In this letter to the editor, Andrew Barber complains about the double talk and lies we get from our Congressmen and Senators who will say anything to get elected.
Using denial-of-service attacks to crash telephone service???
I had not thought about but I guess you could use "denial of service attacks" to knock out police or other government phone lines as in the following article.
N.J. court: Warrants needed for cellphone tracking
N.J. court: Warrants needed for cellphone tracking
NSA director wants private companies to spy on us for the government????
NSA director wants private companies to spy on us for the government????

The problem isn't the Patriot Act, it's the people that passed it.
If the Founders were here I suspect they would tell us that is why they gave us the Second Amendment.Of course just a few days ago a good number of Congressmen and Senators said they were SHOCKED that NSA and the Homeland Security were spying on Americans.
Of course that was just 100 percent political BS to help them get re-elected next time around.
Sadly the members of Congress and the Senate don't work for the American people, they work for the entrenched government bureaucrats like the folks in the NSA, CIA, and Homeland Security. And of course this vote shows their loyalty to the bureaucrats in the NSA, CIA, and Homeland Security.
House votes to continue NSA surveillance program
Wed Jul 24, 2013 4:02 PM
WASHINGTON — The U.S. House of Representatives has voted to continue the collection of hundreds of millions of Americans’ phone records in the fight against terrorism.
The chamber rejected a measure to end the program’s authority. The vote was 217-205 on Wednesday.
Republican Rep. Justin Amash had challenged the program as an indiscriminate collection of phone records. His measure, if approved by the full House and Senate and signed by the president, would have ended the program’s statutory authority.
The White House, national security experts in Congress and the Republican establishment had lobbied hard against Amash’s effort.
Libertarian-leaning conservatives and some liberal Democrats had supported Amash’s effort.
The vote was unlikely to settle the debate over privacy rights and government efforts to thwart terrorism.
Senate pushes sanctions on nations aiding Snowden
SourceSenate pushes sanctions on nations aiding Snowden
Associated PressBy BRADLEY KLAPPER | Associated Press
WASHINGTON (AP) — U.S. sanctions against any country offering asylum to Edward Snowden advanced in Congress on Wednesday as the 30-year-old National Security Agency leaker remained in a Moscow airport while Russia weighed a request for him to stay permanently.
The measure introduced by Sen. Lindsey Graham, R-S.C., demands the State Department coordinate with lawmakers on setting penalties against nations that seek to help Snowden avoid extradition to the United States, where authorities want him prosecuted for revealing details of the government's massive surveillance system. The Senate Appropriations Committee approved the proposal unanimously by voice vote as an amendment to next year's $50.6 billion diplomacy and international aid bill.
"I don't know if he's getting a change of clothes. I don't know if he's going to stay in Russia forever. I don't know where he's going to go," Graham said. "But I know this: That the right thing to do is to send him back home so he can face charges for the crimes he's allegedly committed."
Venezuela, Bolivia and Nicaragua have offered Snowden asylum since his arrival at Moscow's Sheremetyevo airport a month ago, shortly after identifying himself as the source of a series of news reports outlining the NSA's program to monitor Internet and telephone communications. It was believed he would then fly to Cuba. The U.S. then canceled his passport, stranding him, with Russia yet to authorize his request for temporary asylum or allow him to fly on to another destination.
Snowden wants permission to stay in Russia, his lawyer said Wednesday after delivering fresh clothes to his client. It's unclear how long the Kremlin will take to decide on the asylum request.
Graham said Snowden's revelations have had "incredibly disturbing" implications for national security.
The Obama administration says the surveillance has foiled a number of terrorist plots against the United States. It says the public outing of its programs are helping terrorist groups change their tactics.
The case also has sparked tension between Moscow and Washington at a sensitive time, less than two months before President Barack Obama's planned talks with Russian President Vladimir Putin in Moscow and again at a G-20 summit in St. Petersburg.
White House press secretary Jay Carney said Wednesday the U.S. was "seeking clarity" about Snowden's status. The head of the Senate Foreign Relations Committee, Sen. Robert Menendez of New Jersey, warned that "providing any refuge to Edward Snowden will be harmful to U.S.-Russia relations."
The relationship is already strained by a Russian crackdown on opposition groups, American missile-defense plans in Europe and the former Cold War foes' opposing views of the civil war between Syrian President Bashar Assad's regime and rebels.
Government snooping is going too far
SourceGovernment snooping is going too far
By Editorial board The Republic | azcentral.com Fri Jul 19, 2013 5:43 PM
The conflicting interests of national security and public safety on the one hand and individual liberty on the other both have sound arguments that can trump one another.
But these are fast-changing times where these interests are concerned, and a couple of the arguments on the security side are losing credibility.
Such as: If you haven’t done anything wrong, you have nothing to worry about.
Or: The program is extremely limited in scope and narrowly tailored.
Ever since former National Security Agency contractor Edward Snowden began releasing his cache of stolen state secrets, questions about the extent of spying by federal agencies have multiplied. The more we learn about what the feds have learned about us, the more this story is turning against federal snooping.
Last week, top NSA officials testified before the House Judiciary Committee on the hot-button program dedicated to collecting “metadata” from every telephone call made in the United States — a program far more extensive than previously understood.
If the Obama administration has its way, it could grow to include government databases of credit-card purchases, hotel records and Internet use. The committee was not impressed.
“You’ve already violated the law as far as I am concerned,” John Conyers, the panel’s ranking Democrat, told the NSA officials.
Conyers’ provocative declaration was seconded by Republicans, many arriving at the same conclusion: Government snooping agencies are going too far.
Metadata collection is not the exclusive preserve of federal agencies, nor is it restricted to records of telephone calls. As technologies such as image capturing become more sophisticated and cheaper, local police agencies are buying systems that allow them to record and store vast data files on vehicles, including their license plates and their locations at given times.
Since 2005, police agencies in Arizona have purchased such surveillance systems, including Mesa, Peoria, Chandler and Phoenix, as well as the Arizona Department of Public Safety.
Calculated strictly in terms of return on investment, the purchases can turn a healthy “profit.” Mesa bought a system in 2005 for $25,000. Since then, the city has used its image-capturing system to recover more than $2 million worth of stolen vehicles.
Does that justify a program that gives the government knowledge of your every coming and going?
We have reached an age in which an incident not captured on video is seen as the exception, not the norm. You mean with all those people around, no one had a phone camera running?
This “self-surveillance” culture, which has evolved naturally as technology advances, has proved invaluable at times. The images and video produced in the wake of the Boston Marathon bombing come to mind.
The distinction between government databases and information held in private hands was raised at Wednesday’s Judiciary hearing. Why not ask phone companies to retain their own metadata longer, asked Rep. Peter King, R-N.Y. The NSA fellows said they would think about that.
Think about it they should. Americans have a right to expect their government to act to keep them safe from foreign-sponsored harm. That federal duty is enshrined in the Constitution.
Also enshrined in the Constitution is the right to the pursuit of liberty.
There is a tipping point between the two contrasting interests. The intersection of technology and the insatiable desire of governments to exert control tells us we are teetering toward the side of the government simply knowing too damned much.
Border statistics demanded by Arizona's congressional delegation
I guess the goons in the BP are only going to tell us the statistics that makes them look like heroes!!!!Of course they didn't even ask for the statistics on the "war on drugs". Despite the "war on drugs" being almost 100 years old, since the passage of the "1914 Harrison Narcotics Tax Act" you can go to almost any high school in American and buy any illegal drug you want.
Border statistics demanded by Arizona's congressional delegation
By Daniel González The Republic | azcentral.com Sat Jul 27, 2013 12:19 AM
Several members of Arizona’s congressional delegation have called on Homeland Security Secretary Janet Napolitano to release data the government collects about immigrants crossing the border illegally but refuses to make public.
The demands for more information about illegal immigration along the southern border follow an article in The Arizona Republic published July 21.
The article reported that the Department of Homeland Security routinely points to data about the number of Border Patrol apprehensions as a measure of success in reducing illegal immigration. However, the DHS refuses to release or discuss other information gathered on how many migrants evade capture, how many are caught multiple times, and what percentage of migrants successfully enter the U.S. illegally.
Republicans and Democrats from the Arizona delegation expressed concern that the refusal to release data about illegal crossings creates an incomplete and possibly misleading picture of border security. The information is particularly important now as Congress debates an overhaul of the nation’s immigration system. Part of that overhaul includes giving undocumented immigrants a pathway to citizenship contingent on improvements in border security.
“This important article illustrated the fact that one of the most devastating contributors to an unsecure border is the shortage of information,” U.S. Rep. Matt Salmon, R-Ariz., wrote in a July 25 letter to Napolitano.
His letter, prompted by the article, asks for DHS data and studies pertaining to border-crossing recidivism rates, apprehensions and the effectiveness of several strategies the government used to deter illegal immigration and drug trafficking, including fencing, vehicle barriers, electronic alert systems and additional Border Patrol agents.
Rep. Paul Gosar, a Republican, and Rep. Ann Kirkpatrick, a Democrat, also said they plan to contact the DHS asking that more information about illegal border crossings be released.
“In Congress, there is finally a bipartisan, common-sense effort to address immigration reform. Let's seize this moment, it's good for Arizona,” Kirkpatrick said in an e-mail. “I expect a rigorous debate around measurability standards and what constitutes a secure border. Let’s make sure we have all the data and information in front of us, so we can craft good and fair policy.”
Republican Reps. David Schweikert and Trent Franks and Rep. Ron Barber, a Tucson Democrat whose district includes Arizona’s southeastern border with Mexico, said they believe the DHS needs to do a better job of sharing information to ensure that border security is achieved.
“I have been raising this issue since I went to Congress one year ago,” Barber said in an e-mail. “As a ranking member of the Oversight Subcommittee of the Homeland Security Committee, I have questioned officials of the department about their poor communications with the American public and repeatedly called for greater transparency and accountability.”
Barber said he has filed amendments to a border-security bill pending in the House that would require the DHS to hold public meetings to provide critical information to border residents, other community members and the media. The bill would require the DHS to develop a comprehensive strategy for securing the border.
“This process must be followed as DHS develops its border-security strategy and establishes credible and honest measurements of success,” Barber said in the e-mail.
DHS acting press secretary Peter Boogaard said the department would respond directly to members of Congress requesting information about illegal border crossings, “not through the media.”
He said, however, that the DHS relies on multiple methods to measure border security, “each of which paints a different portion of the overall border-security picture and each of which informs tactical decision making.
“In line with this broad focus, the Administration has made significant investments in border security on a number of fronts,” Boogaard said in a written statement. “While no single metric can individually assess the state of border security, the dozens of metrics we use every day clearly demonstrate significant progress and improved quality of life at the border.”
The Republic article by reporter Bob Ortega reported that the DHS has refused to respond to the newspaper’s request for data on the number of migrants who were turned back after crossing the border illegally or got away from the Border Patrol and thus were able to successfully enter the U.S. illegally.
The Border Patrol releases information on the number of apprehensions by agents, but not on the number of migrants apprehended more than once or how many of those apprehensions are the same migrant caught multiple times. The Border Patrol does not release data on “turn-backs” or “got-aways” — people detected by agents or surveillance equipment but not caught.
The article also showed that the DHS has refused to release the same data to outside researchers, including a panel of leading statisticians, economists and demographers at the National Academy of Sciences that conducted a taxpayer-funded study on illegal immigration at the request of the DHS.
The DHS also has refused to release the results of a 2007 report by the Homeland Security Institute that studied border-crossing recidivism and the likelihood of apprehending migrants attempting to cross the border illegally, the article reported. That study, which has been updated annually, also was federally funded.
The article quoted critics who say the DHS’ failure to fully release information about illegal border crossings makes it difficult for outside researchers to analyze the effectiveness of the department’s strategy for securing the border at a time when spending on border security has soared. In the past seven years, the DHS has spent more than $106 billion on border security.
The immigration bill passed by the Senate in late June, and now languishing in the House, would provide an additional $46 billion in border-security spending and add 19,200 more Border Patrol agents along the Mexico border over the next eight years, doubling the current number.
The additional spending and agents would be used to achieve the bill’s goal of achieving an effectiveness rate of “90 percent,” meaning the DHS would capture or turn back nine migrants for every person who got away and successfully entered the country illegally.
Brian Rogers, a spokesman for Sen. John McCain, R-Ariz., said McCain has “long been troubled by the failure of DHS to develop and make public appropriate metrics to measure our success in border security.”
“This lack of disclosure has exacerbated the lack of trust in DHS and this Administration,” Rogers said in an e-mail.
McCain and Arizona’s other senator, Republican Jeff Flake, helped add language in the immigration bill passed by the Senate that includes provisions that require the Border Patrol to report to Congress on a biannual basis objective metrics to help Congress and the public determine how successful the Border Patrol is at apprehending illegal border-crossers.
When he was a member of the House, Flake also tried to get the DHS to develop better ways to measure border security.
“It’s going to be impossible for Congress to tackle immigration reform without achieving operational control of our southern border, and the federal government can’t achieve operational control if they aren’t even using it as a metric,” Flake said in a press release in November 2012, after the House passed a bill requiring the DHS to create for congressional approval a strategy for gaining operational control of the northern and southern U.S. borders.
It's impossible to fire a crooked police chief????
Glendale Police Chief Greg Dominguez threatens to burn down store and kill employees
It's impossible to fire a crooked police chief????Sounds like it.
 Glendale’s assistant police chief Greg Dominguez threatened to burn down Spanky’s Smoke Shop in Peoria for selling “stuff” to his son. Assistant police chief Greg Dominguez also threatened to kill a store employee.
Glendale’s assistant police chief Greg Dominguez threatened to burn down Spanky’s Smoke Shop in Peoria for selling “stuff” to his son. Assistant police chief Greg Dominguez also threatened to kill a store employee.
If a civilian threatened to burn down the Glendale City hall and kill the mayor of Glendale for giving the Coyotes millions of our tax dollars that civilian would be in prison right now. But when the Glendale police chief does the same thing it's no big deal.
Board: Glendale's former assistant police chief should be reinstated
By Miguel Otarola The Arizona Republic-12 News Breaking News Team Thu Jul 25, 2013 5:32 PM
Glendale’s former assistant police chief should get his job back, so said a personnel oversight board Wednesday after reviewing his demotion.
 The city’s Personnel Board voted 3-1 to recommend Greg Dominguez’s reinstatement after a four-and-a-half hour appeal hearing that ended at 10:45 p.m.
The city’s Personnel Board voted 3-1 to recommend Greg Dominguez’s reinstatement after a four-and-a-half hour appeal hearing that ended at 10:45 p.m.
Dominguez was bumped down to commander in April following accusations that he threatened to burn down Spanky’s Smoke Shop in Peoria for selling “stuff” to his son. That stuff, Dominguez later said, was the synthetic drug known as “spice.”
The police report said Dominguez returned to the store and threatened to kill an employee if the store kept selling to his son. Dominguez was off-duty during the incidents and did not announce he was an officer, said David Leibowitz, spokesman for the Glendale chapter of the Fraternal Order of Police. Leibowitz added Dominguez was not wearing his police uniform or driving a patrol car. [So since he didn't commit the crimes while he was wearing the Glendale Police Chief's uniform that means everything is OK????]
In addition to his demotion, Dominguez was suspended for five days without pay by Chief Deborah Black in April following a internal affairs investigation.
The board listened to arguments from the city attorney and Dominguez’s lawyer, Neil Landeen, as well as testimony from Black Wednesday night. In the end, those voting in favor of Dominguez said the punishment was too harsh. [What rubbish!!! Since when is firing a crooked cop for threatening arson and murder too harsh of a punishment. If he was a civilian he would be sitting in jail waiting to go to trial for threatening arson and murder]
The personnel board hears appeals regarding disciplines, according to the Glendale city website. It is made up of five residents appointed by Glendale City Council. [Yea, and they are probably all cops or ex-cops?]
The board’s recommendation will go to City Manager Brenda Fischer, who began her position earlier this week. Fischer has the choice of upholding Black’s demotion or reinstating Dominguez as assistant police chief.
“I’m sure she will want to go forward ... and make a decision sooner rather than later,” said Julie Pendergast, president of the Glendale Chapter of the Fraternal Order of Police.
The police department has two assistant police chief positions. Currently Rick St. John is the only sitting assistant chief and the other position is unfilled. Commander Matthew Lively is serving in the interim.
Dominguez has served with the Glendale Police Department for 28 years, according to the department’s website.
Leibowitz said Wednesday’s recommendation was still not a reason for Dominguez to celebrate.
“This is not time for a victory lap. This is an intermediate step,” he said. “(Greg) is obviously very grateful to have the opportunity to have the city manager decide this case.”
Justin Harris, president of the Glendale Law Enforcement Association, called the personnel board’s decision, “the right call.” [Yea, let one crooked cops be fired, and next thing you know other crooked cops will be fired. Can let that happen. Any member of the police union will tell you it's wrong to fire crooked cops.]
Department officials did not return several calls requesting interviews.
“He is not looking to avoid responsibility of what happened,” Leibowitz said. “He just loves his job.” [What rubbish!!! He is a criminal who should have been fired from his job]
John McCain is against the "military police state"???
Kyrsten Sinema votes to support the military police state???
John McCain is against the "military police state"???That's probably as accurate as Hitler saying he loves Jews.
And allegedly anti-war, anti-police state Kyrsten Sinema seems to have turned into a supporter of the military industrial complex and the police state.
Kyrsten Sinema voted against the bill which would have curbed the NSA surveillance operations.
Kyrsten Sinema when she was an Arizona elected official tried to flush Arizona's medical marijuana program (Prop 203) down the toilet introducing a bill that would have slapped a 300 percent tax on medical marijuana.
McCain: More transparency on NSA
By Dan Nowicki The Republic | azcentral.com Sat Jul 27, 2013 7:51 PM
U.S. Sen. John McCain says last week’s narrow U.S. House vote on the National Security Agency’s phone-record collecting demonstrates the need for President Barack Obama’s administration to better explain the controversial anti-terror program to an anxious public.
The Republican-controlled House voted 217-205 Wednesday to defeat an amendment that would have drastically curtailed the NSA’s snooping practice, which has rattled privacy advocates and civil libertarians across the political spectrum since it was disclosed in early June.
“I think it’s a combination of right and left, but I think it’s a little more than that. And that is, there’s suspicion out there,” McCain, R-Ariz., told The Arizona Republic. “Because I don’t think there has been enough communication with the American people as to exactly what they’re doing and what they’re not doing. In other words, it concerns all of us that the government might be invading our privacy. So there’s going to have to be legislation that calls for greater transparency and sharing of methodology without compromising our ability to defend this country.”
The split in Arizona’s House delegation illustrates how the NSA issue has blurred traditional partisan and ideological lines. Republican U.S. Reps. Paul Gosar, Matt Salmon and David Schweikert joined Democratic U.S. Reps. Raúl Grijalva and Ed Pastor in voting to curb the NSA surveillance operation. Democratic U.S. Reps. Ron Barber, Ann Kirkpatrick and Kyrsten Sinema [looks like the allegedly anti-war peacenik Kyrsten Sinema now supports the police state and military industrial complex] and Republican U.S. Rep. Trent Franks opposed the amendment to essentially kill the program, which was developed as part of the war against terrorism that followed the Sept. 11, 2001, attacks on the World Trade Center and the Pentagon.
“I doubt if there would have been that vote on Sept. 12, 2001,” McCain said.
In other developments:
McCain is continuing to push bipartisan legislation that over four years would phase out the $1 bill and replace it with a $1 coin. He argues the transition would modernize U.S. currency while saving taxpayers billions of dollars and reducing the deficit.
But a gossip columnist for the Hill, a Washington, D.C., newspaper, last week asked him about one constituency that has been cool to the coin idea: strippers and exotic dancers who collect dollar bills as tips during their stage performances.
“Then I hope that they could obtain larger denominations,” McCain told The Hill, eventually adding, “Fives, tens, one hundreds!”
On Friday, McCain clarified to The Republic that he weighed in only when “pressed about the predicament” by the media.
“I was asked about it. ... I don’t frequent those establishments,” McCain said. “I don’t presume to know what’s best. I think I’m an expert on a lot of national-security issues, but that’s one that I’m not really well-versed in.”
McCain’s “a la carte” cable television bill got a boost last week when U.S. Sen. Richard Blumenthal of Connecticut announced that he would sign on as its lead Democratic co-sponsor.
McCain this year revived legislation that would encourage cable and satellite TV providers to offer customers the ability to purchase only the channels they want to watch instead of having to buy an expensive bundle. The bill, which faces stiff resistance from the influential telecommunications industry, remains a longshot to become law, but Blumenthal’s participation could help its chances in the Democrat-controlled Senate.
“We’re having a lot of fun with it,” McCain said. “We’re making those lobbyists earn their salaries.”
Nowicki is The Republic’s national political reporter.
John McCain and Barack Obama working together???
And it ain't about good government. It's kind of like the typical "I will vote for your pork if you vote for my pork" line.Or you could think of it like the Crips and the Bloods working together corner the heroin market in South Central Los Angeles. [Not that I have anything against heroin, I think it should be legalized]
Sadly ever since Barack Obama got elected he pretty much has been a clone of both George W. Bush and John McCain.
Barack Obama and John McCain: Washington's newest odd couple
Posted: Sunday, July 28, 2013 1:14 pm
Associated Press
There was no conciliatory phone call, no heart-to-heart talk to soothe the tensions. No one knows exactly when President Barack Obama and Republican Sen. John McCain went from bitter rivals in the 2008 presidential campaign and foes over health care and national security to bipartisan partners.
Yet in recent months, an alignment on high-profile domestic issues — not to mention an eye on their respective legacies — has transformed Obama and McCain into Washington's most unexpected odd couple. The Arizona senator is a regular visitor to the West Wing and in near-daily contact with senior White House officials.
McCain, in an Associated Press interview, said that he and Obama "trust each other." White House chief of staff Denis McDonough, among the Obama advisers who speak regularly with McCain, praised the lawmaker as a "refreshing" partner who "welcomes a debate and welcomes action."
Like any good business arrangement in the nation's capital, the secret to the new Obama-McCain alliance ultimately comes down to this: Both sides believe that working together is mutually beneficial and carries little political risk.
For Obama, the senator has become a rare Republican backer of important elements on the president's second term agenda, including immigration overhaul, stricter background checks for gun buyers, and perhaps a fall budget deal.
In return, McCain has secured increased access to the White House and an opportunity to redeem his reputation as a Capitol Hill "maverick." That image was tainted when McCain tacked to the right during his failed 2008 presidential run against Obama.
"I've told the people of Arizona, I will work with any president if there are ways I can better serve Arizona and the country," McCain said. "That seems to be an old-fashioned notion but it's the case."
Indeed, the level of attention lavished on a functional working relationship between the Democratic president and the Republican senator underscores how rare such partnerships have been during Obama's tenure.
Lawmakers, including some Democrats, long have chafed at Obama's distant dealings with Capitol Hill and his supposed lack of understanding about how Congress operates.
It's unlikely that Obama and McCain's partnership will lead to a larger detente between the White House and congressional Republicans. While McCain may have sway over some like-minded members of the Senate Republican caucus, he has considerably less influence with his party's more conservative wing, particularly in the GOP-controlled House.
Still, the White House is hopeful that forging policy breakthroughs with McCain and other Senate Republicans will isolate the House GOP and perhaps persuade them to act.
The first test of that strategy probably will be the White House-backed immigration overhaul. McCain helped write and shepherd the bill through the Senate last month. Its future in the House is deeply uncertain.
The administration also will try to work with McCain ahead of impending budget battles, McDonough said, given that the senator and the White House agree there is a negative impact from across-the-board federal budget cuts, particularly on the military and defense industry.
McDonough said it's not just a shared view on policy that has made McCain an attractive partner to Obama on these and other issues. It's their mutual disdain for Washington meetings that never move beyond the standard talking points.
"Part of what's great to work with him is his impatience with that," McDonough said. "You can kind of get into the meat of the matter very quickly"
Obama and McCain were never close during the president's brief tenure in the Senate. While McCain is a creature of Capitol Hill, Obama largely saw Congress as a stepping stone to bigger things. The relationship deteriorated during frequent clashes in the 2008 presidential campaign, and it often appeared during Obama's first term like it would never recover.
In 2010, the two sparred during a televised negotiating session on health care. McCain chastised Obama for brokering deals behind closed doors, to which the president snapped, "We're not campaigning anymore. The election is over."
McCain replied: "I'm reminded of that every day."
White House advisers still bristle over McCain's accusations that the administration covered up details of last year's deadly attacks on Americans in Benghazi, Libya, as well as his relentless criticism of former U.N. Ambassador Susan Rice's role in that alleged effort.
McCain's criticism contributed to Rice's decision to withdraw from consideration as Obama's secretary of state. She now serves as White House national security adviser, a post that does not require Senate confirmation.
McDonough acknowledged that McCain's role in keeping the Benghazi controversy alive has been a source of frustration. But he credited the senator with largely shelving his criticism of Rice once she joined the White House staff.
"The way he's worked with her since she became national security adviser speaks to his interest in making sure that even where we disagree, we're finding a way to work together when we can," McDonough said. "I know the president has appreciated that."
McCain said his stronger ties with the president on domestic issues won't keep him from challenging the president on national security issues, including Syria, where McCain backs a more aggressive U.S. response than does the administration. But he said there's a way to strike an appropriate balance.
"He is the president of the United States," McCain said. "You can strongly disagree and still be respectful."
Low-level staff have access to ‘invasive’ surveillance
Greenwald: Low-level staff have access to ‘invasive’ surveillanceYea, sure - You have nothing to worry about unless you are a criminal. Your emails and phone calls are safe from the prying eyes of government bureaucrats - honest!!!!
Greenwald: Low-level staff have access to ‘invasive’ surveillance
By Aaron Blake, Published: July 28 at 10:57
Glenn Greenwald, the journalist who has worked with Edward Snowden to reveal sensitive national security information, said Sunday that low-level National Security Agency staff and contractors have access to a powerful and invasive tool that can provide them the e-mails and phone calls of basically anybody — up to and including the president.
“The NSA has trillions of telephone calls and e-mails in their databases that they’ve collected over the last several years,” Greenwald said on ABC’s “This Week.”
He then detailed the program, which he said only require an e-mail or an IP address to return data on Americans.“It searches that database and lets them listen to the calls or read the e-mails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you’ve entered, and it also alerts them to any further activity that people connected to that e-mail address or that IP address do in the future,” Greenwald said.
Greenwald, who is set to testify on Capitol Hill on Wednesday, suggested intelligence officials are lying when they say low-level staff have no such access to that information. He said he “defies” intelligence officials to deny the program’s existence.
“It’s an incredibly powerful and invasive tool — exactly of the type that Mr. Snowden described,” Greenwald said.
Appearing on the same show, Senate Intelligence Committee Ranking Member Saxby Chambliss (R-Ga.) cast doubt on Greenwald’s reporting.
“I was back out at NSA just last week, spent a couple hours out there with high-level and low-level NSA officials, and what I have been assured of is there is no capability … at NSA, for anyone without a court order to listen to any telephone conversation or to monitor any e-mail,” Chambliss said.
Chambliss also said any access that low-level staff had to such personal information would be accidental.
“In fact, we don’t monitor e-mails. That’s what kind of assures me is that the reporting is not correct. Because no emails are monitored now,” Chambliss said. “They used to be, but that stopped two or three years ago. So I feel confident that there may have been some abuse, but if it was it was purely accidental.”
Revealers of government secrets share how their lives have changed
After the whistle: Revealers of government secrets share how their lives have changedGovernment of the people, by the elected officials and appointed bureaucrats, for the elected officials, appointed bureaucrats, government employees and special interest groups that helped get them into power.
Sorry Mr. Lincoln, that's how your speech should have been written. The way government really works, is while our rulers are elected by the people, they end up serving the government bureaucrats that work for them, along with the special interest group that helped them get into power.
After the whistle: Revealers of government secrets share how their lives have changed
By Emily Wax, Published: July 28 E-mail the writer
The former high-ranking National Security Agency analyst now sells iPhones. The top intelligence officer at the CIA lives in a motor home outside Yellowstone National Park and spends his days fly-fishing for trout. The FBI translator fled Washington for the West Coast.
This is what life looks like for some after revealing government secrets. Blowing the whistle on wrongdoing, according to those who did it. Jeopardizing national security, according to the government.
Who is Edward Snowden?: A 30-year-old government contractor has been charged with espionage for recent leaks of classified intelligence. He has vaulted from obscurity to international notoriety, joining the ranks of high-profile leakers such as Daniel Ellsberg of Pentagon Papers fame.
Heroes. Scofflaws. They’re all people who had to get on with their lives.
As Edward Snowden eventually will. The former NSA contractor who leaked classified documents on U.S. surveillance programs is now in Russia, with his fate in limbo. The Justice Department announced last week that it won’t seek the death penalty in prosecuting him, but he is still charged with theft and espionage.
Say he makes it out of there. What next, beyond the pending charges? What happens to people who make public things that the government wanted to keep secret?
A look at the lives of a handful of those who did just that shows that they often wind up far from the stable government jobs they held. They can even wind up in the aisles of a craft store.
Peter Van Buren, a veteran Foreign Service officer who blew the whistle on waste and mismanagement of the Iraq reconstruction program, most recently found himself working at a local arts and crafts store and learned a lot about “glitter and the American art of scrapbooking.”
“What happens when you are thrown out of the government and blacklisted is that you lose your security clearance and it’s very difficult to find a grown-up job in Washington,” said Van Buren, who lives in Falls Church and wrote the book “We Meant Well: How I Helped Lose the Battle for the Hearts and Minds of the Iraqi People.” “Then, you have to step down a few levels to find a place where they don’t care enough about your background to even look into why you washed up there.”
The Apple Store employee
“Let’s sit in the back,” Thomas Drake says when choosing a booth at Parker’s Classic American Restaurant in downtown Bethesda during his lunch break from Apple. “I have a lot to say. I was a public servant. That’s a very high honor. It’s supposed to mean something.”
Drake was prosecuted under the World War I-era Espionage Act for mishandling national defense information.
His alleged crime: voicing concernsto superiors after the Sept. 11, 2001, attacks about violations of Americans’ privacy by the nation’s largest intelligence organization (the NSA) and later, in frustration, speaking to a reporter about waste and fraud in the NSA intelligence program. (He says he revealed no classified information.)
He lost his $155,000-a-year job and pension, even though in 2011 the criminal case against him fell apart. The former top spokesman for the Justice Department, Matthew Miller, later said the case against Drake may have been an “ill-considered choice for prosecution.”
Drake, now 56, is tall and lanky and dresses as though he’s ready, at any moment, to go on a gentle hike. He is the type of person who likes consistency. He went to work at Apple the day after the charges against him were dropped, surprising his co-workers who thought he would at least take a day off. In 2010, he got an adjunct professor job at Strayer University but was fired soon after, he says, while he was under government investigation.
“I was just blacklisted,” he said, adding that he started his own company but has only had minor work. “People were afraid to deal with a federal government whistleblower.”
Drake long planned to be a career public servant. He enlisted in the Air Force in 1979 and flew on spy planes and once was a CIA analyst and an expert in electronic intelligence missions. On Sept. 11, 2001, he reported for his first day of work as a senior executive at the NSA’s Fort Meade campus, and shortly thereafter, he voiced “the gravest of concerns” regarding a secret domestic surveillance program that, he says, was launched shortly after the attacks.
Who is Edward Snowden?: A 30-year-old government contractor has been charged with espionage for recent leaks of classified intelligence. He has vaulted from obscurity to international notoriety, joining the ranks of high-profile leakers such as Daniel Ellsberg of Pentagon Papers fame.
In 2006, he was reassigned from the NSA to be a professor at the National Defense University, but he was forced to leave in 2007 when his security clearance was suspended.
Ironically, he was teaching a class called “The Secret Side of U.S. History.”
Now working at the Apple Store and living in Howard County, he is extremely grateful for his hourly wage retail job. He has no choice. He has massive legal debts and a son ready to go to college.
Last year, he was working when he spotted an unlikely customer: Attorney General Eric H. Holder Jr., who came in to check out iPhones.
Drake introduced himself and asked: “Do you know why they have come after me?”
“Yes, I do,” Holder said.
“But do you know the rest of the story?,” he asked.
Holder quickly left with his security detail, Drake said.
“It’s not every day you get to talk to the chief law enforcement officer of the land about your case,” Drake said, “or at least try.”
The author in Oregon
Sometimes Washington is just the last place you can stand to be.
Sibel Edmonds was once described by the American Civil Liberties Union as “the most gagged person in the history of the United States.” And she was a regular on Washington’s protest circuit.
She was fired from her work as a translator at the FBI for trying to expose security breaches and cover-ups that she thought presented a danger to U.S. security. Her allegations were supported and confirmed by the Justice Department’s inspector general office and bipartisan congressional investigations, but she was not offered her job back.
She also published a memoir, “Classified Woman — The Sibel Edmonds Story.”
Then last summer, Edmonds, 43, decamped with her 5-year-old daughter and husband to Bend, Ore., which is known as the sunny side of the state. The July weather is 77 degrees without humidity, and there are 33 independently owned coffee shops and nine microbreweries.
“I am touring every single one. Plus, we don’t even have air conditioning here,” she said. “We open the windows and feel the breeze.”
For years before she left, Edmonds found Washington’s atmosphere suffocating. Many of her neighbors in Alexandria were lobbyists and contractors, who she says stopped talking to her after her name appeared in the newspaper.
Luckily, her husband of 21 years is a retail consultant and can live anywhere. She says that most whistleblowers have spouses who work in the same agencies, which typically puts pressure on their marriages.
She is still dedicated, she says, to the cause of exposing injustice and making information free. She spends hours running “Boiling Frog Post: Home of the Irate Minority,” a podcast and Web site that covers whistleblowing and tries to create broader exposure for revelations. She is also founder and director of the National Security Whistleblowers Coalition.
“I think in the current climate, Congress and Washington is a last resort,” she said. “We are going directly to the people and focused on releasing information. And I don’t have to do that from Washington.”
Who is Edward Snowden?: A 30-year-old government contractor has been charged with espionage for recent leaks of classified intelligence. He has vaulted from obscurity to international notoriety, joining the ranks of high-profile leakers such as Daniel Ellsberg of Pentagon Papers fame.
The alienated fly fisherman
“The connection is really bad, it must be the NSA surveillance program,” Richard Barlow says jokingly when speaking to a reporter on his cellphone from his motor home outside Yellowstone National Park.
“I’m out here with the grizzly bears,” he says. “But this is where I’m comfortable. I’m a 58-year-old seriously damaged, burned-out intelligence officer.”
Barlow says he suffers from chronic PTSD, which makes it hard for him to deal with stress and sometimes other people. He finds comfort in his three dogs: Sassy, Prairie and Spirit.
His supporters say that shouldn’t be surprising considering what he went through.
Barlow started his career as a rising star tasked with organizing efforts to target Pakistan’s clandestine networks for acquiring nuclear materiel. He won the CIA’s Exceptional Accomplishment Award in 1988 for work that led to arrests, including that of Pakistani nuclear scientist A.Q. Khan.
He testified before Congress under direct orders from his CIA superiors, but he says he later became the target of criticism from some people in the CIA who were supporting the mujahideen (including Osama bin Laden at the time) in efforts to push the Soviets out of Afghanistan.
He says he chose to leave the CIA, and in early 1989, he went to work as the first weapons-of-mass-destruction intelligence officer in the administration of President George H.W. Bush. Barlow continued to write assessments of Pakistan’s nuclear weapons program for then-Defense Secretary Dick Cheney. He concluded that Pakistan already possessed nuclear weapons, had modified its F-16s to deliver these weapons and had continued to violate U.S. laws.
The intelligence would have legally precluded a sale of $1.4 billion worth of additional F-16s to Pakistan.
But in August 1989, Barlow learned that the Defense Department had asserted that the F-16s were not capable of delivering Pakistan’s nuclear weapons. Barlow said that Congress was being lied to, and he objected internally.
Days later, he was fired.
“Back then I was disgustingly patriotic and I thought the government is allowing Pakistan to develop and spread nuclear weapons and I got destroyed for trying to stop it,” he said.
He was 35 at the time. His marriage to his 29-year-old wife, who also worked at the CIA, was shattered.
After a 1993 probe, the inspector general at the State Department and the CIA concluded that Barlow had been fired as a reprisal. The Defense Department maintained that the Pentagon was within its rights to fire Barlow. A 1997 GAO report largely vindicated Barlow, and his security clearances were restored. But, he says, he was unable to get rehired permanently by the government because his record was smeared.
He eventually found some work as a consultant, helping to start and run the FBI’s counterproliferation program out of Sandia National Laboratories.
Meanwhile, he has been trying for years to collect the $89,500 annual pension and health insurance that he thinks he is owed.
Who is Edward Snowden?: A 30-year-old government contractor has been charged with espionage for recent leaks of classified intelligence. He has vaulted from obscurity to international notoriety, joining the ranks of high-profile leakers such as Daniel Ellsberg of Pentagon Papers fame.
Much of what he tried to report about Pakistan’s nuclear program is common knowledge today, and several national security bestsellers have included his story, including George Crile III’s 2003 book “Charlie Wilson’s War: The Extraordinary Story of the Largest Covert Operation in History,” which describes Barlow as a “brilliant young analyst who gave devastating testimony.”
Today, the consulting work has dried up. He has run out of money and thinks he is about a month from being homeless.
“I served my country for 23 years. I could go get a job for $10 at Wal-Mart,” he said. “But that’s not the issue, the issue is where’s my money?”
Despite efforts by senators and various legislative committees to get him compensated for his loss, the issue has never been resolved, for political and bureaucratic reasons.
He thinks part of the problem is that there’s no structure to compensate whistleblowers in the intelligence field. He also says that the Obama administration has criminalized whistleblowing on levels he’s never seen before.
Today, he spends his days in the wilderness, fly-fishing and bird hunting with his dogs.
The advocate
It’s 8 a.m. on the 11th floor of a K Street office building, and Jesselyn Radack, 42, is trying to tame her curly blond hair with a straightening iron.
“Our PR people said, ‘Straight hair is serious hair,’ ” she said, laughing. “But it is like 100 degrees outside.”
Radack is an attorney and former ethics adviser for the Justice Department. Her supervisor told her to find another job after she disclosed after Sept. 11 that the FBI interrogated John Walker Lindh, known as the “American Taliban,” without an attorney present. Her case was closed in 2003, and prosecutors never identified a potential charge against her.
Today, Radack is a mother of three and director of national security and human rights at the Government Accountability Project, a whistleblowing advocacy organization.
That means she’s an advocate, attorney and, it turns out, therapist of sorts for whistleblowers who come to her “bankrupt, blacklisted and broken,” she says.
“Once you are labeled that way, you are just radioactive,” she said.
And she can certainly empathize.
Before she decided to make her disclosure, she says she suffered from horrible insomnia. She also has long suffered from multiple sclerosis, and the stress caused flare-ups of her disease.
“I had this knowledge and had to do something,” she said on a recent afternoon at her brick home in Tenleytown. “After law school, I thought the government wears the white hat and is on the right side of the law. I never expected to be a whistleblower.”
But the Yale Law School graduate saw something she thought was wrong and felt compelled to report it.
After her case went public, she noticed a chill in how she and her family were treated. She took her children to the “tot shabbat,” or sabbath celebration for young children, at Temple Sinai in Northwest Washington and noticed that no one would sit near her and her family. It turns out that some of the people she blew the whistle on also attended her temple. The situation got so bad, she said, she had to talk to the rabbi about it.
“We’re inside the Beltway, and it’s a small city,” Radack says. “It’s like high school. They just freeze you out.”
Secret surveillance court overhaul is urged
Personally I suspect the program has ALWAYS been unconstitutional and never should have been created. But even if the program is constitution, which I doubt, this article points out some flaws.the Justice Department submitted 1,789 requests to "conduct electronic surveillance." One was later withdrawn, and each of the rest was approved by a judge
Blumenthal has described the court as "broken. It is unaccountable, secretive and one-sided."
Secret surveillance court overhaul is urged
By David G. Savage
July 29, 2013, 5:00 a.m.
WASHINGTON — When the Foreign Intelligence Surveillance Court began in 1978, it was seen as a smart compromise aimed at protecting both national security and civil liberties.
Before, the FBI under Director J. Edgar Hoover or the U.S. attorney general could use secret wiretaps to compile damaging dossiers on perceived enemies, including politicians and activists. Under the new law, the FBI or the CIA had to go before a judge of the special court if it wanted to wiretap an "agent of a foreign power" in this country, such as a Soviet spy.
These days, the Foreign Intelligence Surveillance Court is more often seen as a good idea gone sour.
As the U.S. government has shifted away from tracking spies or known terrorists to detecting potential plots linked to terrorism, the judges on the court have been called upon to make momentous decisions, such as approving the mass collection of records and data.
Critics say the judicial process has gone awry. The judges, who once served as a check on the government, now serve as a secret and secure rubber stamp for wide-ranging surveillance policies, they say.
"This court has evolved to serve a very different role than when it began," said Jennifer Granick, a lawyer at the Stanford Center for Internet and Society. "It is now making secret interpretations of the law, and no judge, and no court, should play that role."
She was referring to leaks last month that revealed how the government's surveillance has expanded in the last decade. One document released by intelligence analyst Edward Snowden showed that a judge on the secret court had approved an order that required a unit of Verizon to turn over all its phone records for a three-month period.
This revelation surprised many, but not those inside the government. Since 2001, Congress has authorized federal agents investigating "international terrorism" to obtain business records that are "relevant to an authorized investigation."
This read as though it referred to records involving known terrorists or at least suspicious people with links to terrorists.
Instead, the Justice Department under President George W. Bush and now President Obama decided this meant the National Security Agency could collect and store all the dialing records of phone calls made in this country because they might prove relevant to a future terrorism investigation.
The mass collection policy was approved by a judge of the Foreign Intelligence Surveillance Court in a secret hearing with only the government's lawyers present.
This has prompted calls in Congress and elsewhere for changes in the court. Some cite a need for a better mix of judges than those currently serving, who are almost all Republican appointees. Others want to include an advocate who takes the other side and argues for privacy and civil liberties.
"This process needs an adversary," retired Judge James Robertson, who served on the special court, told an oversight board hearing this month. "A judge needs to hear both sides of a case."
By law, the court is made up of 11 U.S. district judges, all of whom are appointed by Chief Justice John G. Roberts Jr. They rarely meet as a group. Instead, a judge comes to Washington and serves for a week at a time at the federal courthouse to review and act on the government's requests for surveillance.
Last year, the Justice Department submitted 1,789 requests to "conduct electronic surveillance." One was later withdrawn, and each of the rest was approved by a judge, according to a report sent to Congress.
In addition, the government sought 212 orders for "certain business records." The special court "did not deny, in whole or in part, any such application" last year, the Justice Department said, but there were "modifications" to 200 of those orders.
Rep. Adam B. Schiff (D-Burbank) and Sen. Richard Blumenthal (D-Conn.) are proposing measures to change how the judges are named and to require the court to issue unclassified versions of its opinions.
"I think these judges take their jobs very seriously, but we need a more effective set of checks and balances," Schiff said. "Right now, 10 of 11 were appointed by Republican presidents." [Yea, and President Obama, a Democrat, is more or less a carbon copy clone of Republican President George W. Bush.]
Schiff proposes that the judges be nominated by the president specifically for the court and confirmed by the Senate. "If they came before the Senate, we would get a better understanding of how they view the 4th Amendment" and its protection against unreasonable searches, he said. [Yea, like the Senate gives a rats *ss about the Fourth Amendment]
Blumenthal has described the court as "broken. It is unaccountable, secretive and one-sided."
In recent week, lawyers for the Bush and Obama administrations have come to the defense of the special court and its judges. The judges bring a "healthy skepticism" to requests for surveillance, said Steven Bradbury, a top Justice Department lawyer under Bush.
"I want to correct the erroneous claim that the FISA court is a rubber stamp," Robert Litt, counsel for Obama's director of national intelligence, said in a speech at the Brookings Institution. He said the judges made sure each request for surveillance "complies with the law." [Yea, so approving 1,789 of the 1,789 requests to "conduct electronic surveillance" isn't a rubber stamp???]
But University of Virginia law professor Christopher Sprigman, like Granick, says the problem goes beyond how the judges are appointed or how they handle specific requests for wiretapping. He says the major decisions on the nation's surveillance policies should not be made behind closed doors in a one-sided proceeding.
The leaked court orders reveal a mass collection policy that "has no limits," he said. It could include all credit card records or all travel records, he said.
"We need a public debate if we are going to switch to a mass surveillance policy," Sprigman said. "Congress needs to decide — in public — whether it is worth surveilling everyone. This shouldn't be decided in a secret court." [Congress doesn't need a public debate on the best way to side step the Constitution, it needs to start obeying the Constitution!!!]
david.savage@latimes.com
Corporate welfare at Tempe Town Lake!!!!
Corporate welfare at Tempe Town Toilet!!!!
I have these problems with Tempe Town Toilet or Tempe Town Lake as the royal members of the Tempe City Council call it.1) A large part of the time the park is not open to the public, but used for events to raise money for the royal rulers of Tempe. And these events are expensive to attend and most of the working class people that live in Tempe can't afford to attend the events, despite the fact that these people were forced to pay for Tempe Town Toilet with their hard earned tax dollars.
2) These events cause huge traffic jams and parking problems in the downtown Tempe area
3) When these events are concerts they routinely keep people awake late at night in the entire downtown area, and as far north as Roosevelt Road in Scottsdale which is also Continental Drive in Tempe. I am not sure how far south the concerts can be heard.
Also check out:
-----Tempe to weigh revising Town Lake plan
By Dianna M. Náñez The Republic | azcentral.com
Tue Jul 30, 2013 12:10 AM
The Tempe City Council took a leap of faith more than a decade ago when it sank $44.8 million into building a 2 1/2-mile-long lake in the desert.
The council hoped that risking the debt to create high-profile waterfront property would pay off in the long run for Tempe, then a landlocked city desperate for new development.
But 14 years after the lake opened in 1999, city finance officials say Tempe is faced with a reality check that Town Lake is far from reaching the city’s development goals.
Tonight, the council is expected to consider revising a financing plan for Town Lake.
City finance officials have said the revised plan would give developers a financial break on their share of costs tied to the man-made lake [i.e. - stiff us taxpayers with the cost], make private development more affordable [i.e. stiff us taxpayers with the cost] and, ultimately, advance Tempe’s plans to secure sufficient lakeshore private development to ease the hefty public costs of maintaining Town Lake. [now the last phrase certainly is an oxymoron - give tax dollars private developers to lower the cost to taxpayers - now that's an impossibility - the more we give them the more it costs us]
But critics argue that taxpayers have long carried the financial burden for private lake development.
The new plan offers no guarantee that economic breaks for developers will actually spur construction, argue Joe Pospicil and Art Jacobs, two longtime Tempe residents who regularly question city finances and criticize lake expenses.
If approved, the revised plan also would shift the burden of paying for a new west-end lake dam, which the city has estimated will cost at least $37.4 million, to Tempe taxpayers, freeing developers from sharing the expense to replace the dam. [That a fancy way of saying give boatloads of our hard earned tax dollars out in corporate welfare rich corporations - the rich corporations that give bribes, oops, I mean campaign contributions to the members of the Tempe City Council]
Approval of the city proposal would mark the second time a Tempe City Council, aiming to drive development, has tweaked the original 1995 lake-financing plan in favor of developers. The first was in 1997.
Mayor Mark Mitchell said he believes the proposal merits more time in the public realm so that council members may gain sufficient community feedback. [Translation - he wants to make it look like the taxpayers approve of the members of the Tempe City Council giving boatloads of our cash to the rich corporations that gave the members of the Tempe City Council bribes, oops, I mean campaign contributions]
But it remains to be seen whether Mitchell’s colleagues agree that the council has a responsibility to arrange future forums for the public to question and comment on the proposal.
As of Monday, the proposed changes were included on the agenda for today’s council meeting.
The finance proposal is not set for a two-hearing process, which would have allowed for public comment at the first hearing and then required a vote and a second opportunity for public comment at a future council meeting.
That means the council could choose to approve the revised Town Lake financing plan with little opportunity for public input.
But before the council agenda was posted on the city’s website Friday, Mitchell said he still had questions about the financing plan.
“When we initially developed the lake, we had a plan, but it’s a working document,” he said. “We might change it, we might not. (But) we’ll have enough time to thoroughly review (any formal changes).” [translation - we know how to run your life better then you do, but if we screw it up don't blame us]
Mitchell said he expects staff today to merely explain the long-term impact of the proposed changes. [That pretty simple Mayor Mitchell, you and the other royal members of the Tempe City Council will be giving our hard earned tax dollars out as corporate welfare for years to come to corporations that give you bribes, oops, I mean campaign contributions]
The proposed finance changes were triggered by an economic reality check, Roger Hallsted, the city finance analyst for the Rio Salado Community Facilities District, told The Arizona Republic.
“From all of our original projections, (we were) thinking really by about this time ... the lake would be built out,” Hallsted said.
Tempe’s goal is for private development on 120 acres to generate assessment fees covering 60 percent of annual operations costs. [So us taxpayers will be forced to pay for 40 percent of the developers costs]
But a Republic analysis last year revealed that in the 13 years since the lake was filled, private development still only covered about 20 percent of operation and maintenance costs, well below the 60 percent envisioned in the original city plan. [So in stead of us taxpayers being stuck with paying 40 percent of the developers costs, we are stuck with paying 80 percent of the developers costs - if you ask me us taxpayers are getting screwed on this deal]
Tempe taxpayers have and continue to pay the majority of the $2 million to $3 million in annual costs for operations and maintenance as well as most of the bill for the $44.8 million in original construction costs. [translation - us taxpayers are getting screwed - also did you know that the city of Tempe spends more on Tempe Town Toilet, aka Tempe Town Lake then on all the other parks in Tempe combined???]
Private investment has spurred construction of about 24 acres of condos, high-rise office and commercial space around the lake. Town Lake supporters blame the recession for slower-than-expected development. [Well why didn't the freaking geniuses on the Tempe City Council figure out this??? I guess they were too busy taking bribes, oops, I mean campaign contributions from the rich developers]
The proposed changes to the financing plan are aimed at making land surrounding Town Lake more attractive to private development, Hallsted said. [yea, like giving then 10 times as much corporate welfare as originally planned]
If the council approves the changes, Town Lake developers would pay less toward their share of payments for the original construction costs. [And us taxpayers get screwed again and will have to make up the difference]
The proposal emanated from Tempe’s Enhanced Services Commission, Tempe Finance Manager Ken Jones said. [It sounds more like it came from the developers who will be getting the corporate welfare if you ask me!!!!]
The commission includes representation from Jones; Town Lake developers; Nancy Hormann, the president of the group that manages the downtown Tempe district; and Arizona State University, which owns and is attempting to develop acres of lakeshore property. [yes I was right, it did come from the developers who will are getting the corporate welfare!!!!]
A Republic review of public records from the commission meetings shows that commission members have spent the past year discussing development and maintenance plans for the lake.
At a January meeting, Jones asked for “the logic behind asking the council to cover the cost of replacing the dams,” according to public records of the meeting. [If you remember it was the idiots on the Tempe City Council who get screwed on the damn. The accepted a worthless ORAL 30 year guarantee on the damn, which failed after 10 years causing us taxpayers to get stuck with the replacement costs]
Hallsted said shifting the cost of the dams from being a shared debt with private developers to a taxpayer-only-funded cost is the result of the original rubber dam deteriorating years earlier than expected. [yea, like I just said]
“These new dams, at $38 million to $50 million, if we were to put that in at the true cost, just the (Town Lake) infrastructure replacement budget would have gone from $531,000 (annually) to $2 million,” he said.
The city had to face facts, he said, that it would have to shoulder the dam’s cost rather than “bankrupting every single (lake) property owner,” Hallsted said. [f*ck you!!!! bankrupt the developers for making dumb decisions, not the taxpayers. Or let the members of the Tempe City Council pay for the whole thing.]
The commission questioned whether it’s “more expensive to build at the lake than anywhere else in the Valley” and whether the city was “willing to offer an incentive to level the playing field,” according to public meeting records. [Well maybe the idiots on the Tempe City Council should not have build the lake, since it is a money losing experience]
The commission recommended a plan that would lower an annual “holding fee” of sorts that developers pay until they build on their lake property. [translation - make the taxpayers pay more of the developers expenses - i.e. more corporate welfare for the rich corporations building stuff on Tempe Town Toilet]
If the revised plan is approved, that fee would be reduced from the current 5 percent to the rate of inflation, which is currently 2.2 percent, Hallsted said. [which the Tempe taxpayers will pay]
The financing proposal also includes lowering the annual interest rate developers pay over the 25 years they are allowed to pay back their share of lake construction. [again, which the Tempe taxpayers will pay]
The current interest rate is 5 percent, and the proposal would lower it to 3.64 percent, Hallsted said. He added that the proposal calls for the council to make the rate reduction retroactive to July 1, 2009.
If the council approves rolling back the fee, developers that have built existing commercial and residential development at the lake would receive credits on biannual debt payments they are currently making. [and us taxpayers will be stuck with even bigger bills. Of course the members of the Tempe City Council will get to keep the bribes, oops, I mean campaign contributions they accepted from the developers of property at Tempe Town Toilet]
While critics worry that taxpayers are funding too much of the cost for Town Lake, Hallsted reasons that the revised plan will establish a realistic financing plan for the lake and encourage development that will help pay a greater share of the lake’s annual operations and maintenance costs. [why expect the developers to pay for their costs, when they can give small bribes, oops, I mean small campaign contributions to the Tempe City Council members who will stiff the taxpayers with the bill]
“The key thing,” he said, “is being fair to the citizens, but try to make it more enticing for developers to come in.” [translation - the key to this is SCREWING the taxpayers and forcing them to pay the developers bills]
The NSA hears and sees everything you do!!!!!
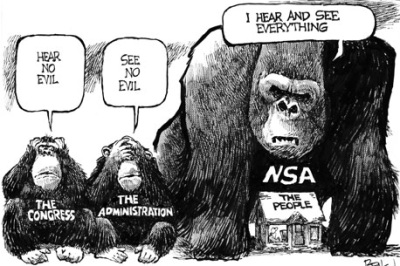
Eugene Robinson: Snowden deserves our thanks, not our derision
SourceEugene Robinson: Snowden deserves our thanks, not our derision
Updated: 29 July 2013 11:44 PM
Edward Snowden’s renegade decision to reveal the jaw-dropping scope of the National Security Agency’s electronic surveillance is being vindicated, even as Snowden himself is being vilified.
Intelligence officials in the Obama administration and their allies on Capitol Hill paint the fugitive analyst as nothing but a traitor who wants to harm the United States. Many of those same officials grudgingly acknowledge, however, that public debate about the NSA’s domestic snooping is now unavoidable.
This would be impossible if Snowden, or someone like him, hadn’t spilled the beans. We wouldn’t know that the NSA is keeping a database of all our phone calls. We wouldn’t know that the government gets the authority to keep track of our private communications — even if we are not suspected of terrorist activity or associations — from secret judicial orders issued by a secret court based on secret interpretations of the law.
Snowden, of course, is hardly receiving the thanks of a grateful nation. He has spent the last five weeks trapped in the transit zone of Sheremetyevo Airport outside Moscow. Russian officials, who won’t send him home for prosecution, wish he would move along. But he fears that if he takes off for one of the South American countries that have offered asylum, he would risk being intercepted en route and extradited. It’s a tough situation, and time is not on his side.
You can cheer Snowden’s predicament or you can bemoan it. But even some of the NSA’s fiercest defenders have admitted, if not in so many words, that Snowden performed a valuable public service.
Less than two weeks ago, the office of Director of National Intelligence James Clapper issued a public statement to announce that the secret Federal Intelligence Surveillance Court has renewed the government’s authority to collect metadata about our phone calls. This was being disclosed “in light of the significant and continuing public interest in the … collection program.”
Isn’t that rich? If the spooks had their way, there would be no “continuing public interest” in the program. We wouldn’t know it exists.
The new position espoused by President Barack Obama and those who kept the NSA’s domestic surveillance a deep, dark secret is that of course we should have a wide-ranging national debate about balancing the imperatives of privacy and security. But they don’t mean it.
I know this because when an actual debate erupted in Congress last week, the intelligence cognoscenti freaked out.
An attempt to cut off funding for the NSA’s collection of phone data, sponsored by an unlikely pair of allies in the House — Justin Amash, a conservative Republican, and John Conyers, a liberal Democrat, both from Michigan — suffered a surprisingly narrow defeat, 217-205.
The Amash-Conyers amendment was in no danger of becoming law — the Senate would have killed it, and if all else failed, Obama would have vetoed it. But it put the intelligence establishment on notice: The spooks don’t decide how far is too far. We do.
At the heart of the Fourth Amendment is the concept that a search must be justified by suspicion. Yet how many of those whose phone call information is being logged are suspected of being terrorists? One in a million?
Equally antithetical to the idea of a free society, in my view, is the government’s position that we are not even permitted to know how the secret intelligence court interprets our laws and the Constitution. The order that Snowden leaked — compelling a Verizon unit to cough up data on the phone calls it handled — was one of only a few to come to light in the court’s three decades of existence. Now there are voices calling for all the court’s rulings to be released.
We’re talking about these issues. You can wish Edward Snowden well or wish him a lifetime in prison. Either way, you should thank him.
Washington Post columnist Eugene Robinson may be contacted at eugenerobinson@washpost.com.
Enjoying that wonderful feeling of security in America

Government Tyrants 1 - Freedom Fighters 0
Bradley Manning convicted of some charges
SourceBradley Manning acquitted of most serious charge, convicted of others
By Richard A. Serrano
July 30, 2013, 8:51 p.m.
FT. MEADE, Md. — Army Pfc. Bradley Manning was convicted Tuesday of violating the Espionage Act and faces up to 136 years in prison, but his acquittal on the even more serious charge of aiding the enemy was hailed as a victory for the press and the Internet against the government's crackdown on leaks of classified information.
Manning's leak of more than 700,000 State Department cables, terrorism detainee assessments, combat logs and videos was the largest breach of classified secrets in U.S. history. Among the information was a now-infamous 2007 video of an Apache combat helicopter attack in Iraq in which U.S. soldiers fired on civilians and killed 12, including two Reuters journalists.
Manning becomes one of only two people ever convicted under the Espionage Act for making classified data available to the public; the other, Samuel L. Morison, a government security analyst convicted in 1985, was pardoned by President Clinton on his final day in office.
"We won the battle, now we need to go win the war," said chief defense lawyer David Coombs, who was greeted by applause and thanks from Manning supporters when he left the courtroom. "Today is a good day, but Bradley is by no means out of the fire."
Under the aiding the enemy charge, Manning, 25, could have been sent to prison for life with no parole. The military judge, Army Col. Denise Lind, heard the case without a jury and did not explain her verdicts. She appeared to have accepted defense arguments that Manning did not understand that releasing the material could allow Al Qaeda and other foreign terrorist organizations to use the information to harm the United States.
The government's theory — that even if Manning did not directly convey information to an enemy, he could be charged with that crime because information released to the public could be obtained by U.S. adversaries — had serious implications for whistle-blowers and those who provide information about classified programs to journalists.
Prosecutors "pushed a theory that making information available on the Internet — whether through WikiLeaks, in a personal blog posting, or on the website of the New York Times — can amount to 'aiding the enemy,'" said Widney Brown, senior director for international law and policy at Amnesty International. That, Brown said, "is ludicrous."
A conviction for aiding the enemy would have "severely crippled the operation of a free press," said Thomas Fiedler, dean of the College of Communication at Boston University.
At Tuesday's hearing, Manning wore a blue dress uniform, wire rim glasses and a prison pallor after three years in pretrial confinement. He stood at ramrod attention and listened without emotion as the judge read the guilty and not-guilty verdicts on about two dozen charges.
A sentencing hearing is scheduled to begin Wednesday, with each side expected to present about 10 witnesses. Manning's lawyers may put him on the stand.
If so, it would be the second time he has addressed the court. In February, Manning pleaded guilty to 10 lesser charges of mishandling classified data. He said then that after collecting intelligence on the wars in Iraq and Afghanistan, "I began to become depressed with the situation we had become mired in year after year."
After the sentencing, Maj. Gen. Jeffrey S. Buchanan, commander of joint forces in the capital region, has the authority to toss out some or all of the guilty verdicts and, theoretically, release Manning. On Friday, Manning supporters rallied outside the gate of Ft. McNair in Washington, where Buchanan is stationed. They carried balloons and a 20-foot banner that read, "Maj. Gen. Buchanan, Do the Right Thing. Free Bradley Manning."
Manning was arrested in spring 2010 after the documents he took from government computer databases began appearing in sensational posts on the WikiLeaks website. For months he was held incommunicado, and his lawyers complained he was kept naked and tortured emotionally before his trial began in June.
Manning elected to allow Judge Lind to hear the case without a jury, probably worried that a panel of fellow soldiers weighing his fate would not be pleased that some of the material he gave to WikiLeaks was found in Osama bin Laden's compound in Pakistan after the Al Qaeda leader was killed by Navy SEALs in May 2011.
Military prosecutors presented evidence that Manning underwent extensive training about safeguarding classified data before becoming an Army intelligence analyst in Iraq, and that he instructed other soldiers in security procedures.
"He was a traitor, a traitor who understood the value of compromised information in the hands of the enemy and took deliberate steps to ensure that they, along with the world, received it," Maj. Ashden Fein, the chief prosecutor, told the judge.
The defense, however, portrayed Manning as a small-town youth from Oklahoma who joined the Army with good intentions, only to become deeply bothered when he discovered what he believed to be government misconduct. Coombs said Manning was a whistle-blower, a "young, naive, good-intentioned soldier."
The soldier has spawned a worldwide group of sympathizers who have rallied in his defense, urged his release and floated his name for the Nobel Peace Prize.
On Tuesday morning, hours before Manning learned his fate, two dozen supporters, many wearing black "TRUTH" T-shirts, hoisted signs and waved at workers arriving at Ft. Meade, where the court-martial has been held, and which also houses the highly secretive National Security Agency and the Defense Information Systems Agency.
Julian Assange, the founder of WikiLeaks, was asked before the verdicts whether a long prison sentence would be worth it to Manning.
"That's something Bradley Manning has to weigh up," Assange told CNN. "He was willing to take that risk because he believes apparently that the result is so important."
richard.serrano@latimes.com
Egyptian military plays Uncle Sam as Uncle Sap
SourcePosted on July 30, 2013 5:20 pm by Robert Robb
Egyptian military plays Uncle Sam as Uncle Sap
Egyptian General Sisi is sure making it hard for his U.S. apologists.
According to the apologists, the military was simply channeling the Rousseauian General Will of the Egyptian people. They were tired of being governed by President Mohamad Morsi and the Muslim Brotherhood, so the military ousted him.
The fact that Morsi had been elected to the position was a triviality. The military would turn civilian power over to a technocratic government, new elections would be held shortly. Nothing to see here. Keep the $1.3 billion in military aid flowing.
Then last week, Sisi gave a public speech exhorting the Egyptian people to flood the streets to give the military a mandate to crush the Brotherhood. So much for the façade of a technocratic civilian government.
Egypt is now run by a military junta. In reality, it has been since a coup by another general, Gamel Nasser, in 1952.
The Egyptian military is grossly oversized. There is no external threat to Egypt’s territorial sovereignty that requires a military of its size and lethality. Its primary mission is clearly internal control.
Nor is the military a neutral force. It controls a huge swath of Egypt’s private sector economy. It has a privileged position it will act to protect.
The United States has heavily subsidized Egypt’s oversized military. According to U.S. law, the aid should be cut off if the military has conducted a coup against a democratically-elected government.
Morsi was elected. The military ousted him, and still holds him hostage. It was a coup.
Moreover, the repression in Egypt mounts. Trumped up charges are being leveled against Morsi. The military has reasserted the Mubarak-era power to arrest civilians. Mubarak’s secret police are being unleashed against internal dissent, principally the Brotherhood.
Yet, the Obama administration says that nothing in the law requires it to decide whether what has happened in Egypt amounts to a coup, so it isn’t going to. Which means that the U.S. military aid will continue to flow to a repressive military junta.
According to the foreign policy “realists” in both political parties, the aid needs to continue so that the United States can retain “leverage” on the junta. Not sure how much leverage we’re buying, but to the extent we are, to what end?
The aid originated in the 1979 peace agreement between Egypt and Israel. Supposedly, it is necessary to keep Egypt honoring the agreement. But Egypt doesn’t pose a threat to Israel. The last thing the Egyptian military wants to do is fight someone with the capability of actually fighting back. Nor does it have an incentive to aid Hamas’ or Hezbollah’s efforts against Israel. They are on the other side of the Arab divide.
So, what might we want to achieve with our leverage in terms of Egyptian domestic affairs?
The Obama administration wants the Muslim Brotherhood to be part of the new political process. But the Brotherhood has already won three national elections. Why should it play a game the military has made clear they will not be permitted to win? And the military is obviously committed to suppressing and enfeebling the Brotherhood, not giving it a role in the country’s future.
U.S. foreign policy should advance our interests, not necessarily our ideals. But there should be clear interests at stake when we trash our ideals.
The coup was supposedly in our national interest because the Muslim Brotherhood wasn’t really interested in democratic governance, but in imposing some sort of Islamist state. But in the worst nightmare of the realists, the Brotherhood wouldn’t impose as repressive a theocratic regime as exists in Saudi Arabia, which the realists regard as an ally.
The geopolitical crosscurrents in the Middle East are powerful, dangerous and blindingly complex and intricate. There is the Sunni-Shia conflict. There is the conflict between the royalists and those, such as the Brotherhood, whose governing philosophy is murky but doesn’t include hereditary succession. Where U.S. interests lie in this maelstrom is far from clear.
What is clear is that no important national interest is being served by continuing to give a repressive military junta $1.3 billion a year. The Egyptian military is playing Uncle Sam for Uncle Sap.
Warrantless Cellphone Tracking Is Upheld
RIP - Fourth Amendment - Warrantless Cellphone Tracking Is Upheld
SourceWarrantless Cellphone Tracking Is Upheld
By SOMINI SENGUPTA
Published: July 30, 2013 88 Comments
The ruling is the first that squarely addresses the constitutionality of warrantless searches of the historical location data stored by cellphone service providers.
The closely watched case, in the United States Court of Appeals for the Fifth Circuit, is the first ruling that squarely addresses the constitutionality of warrantless searches of historical location data stored by cellphone service providers. Ruling 2 to 1, the court said a warrantless search was “not per se unconstitutional” because location data was “clearly a business record” and therefore not protected by the Fourth Amendment.
The ruling is likely to intensify legislative efforts, already bubbling in Congress and in the states, to consider measures to require warrants based on probable cause to obtain cellphone location data.
The appeals court ruling sharply contrasts with a New Jersey State Supreme Court opinion in mid-July that said the police required a warrant to track a suspect’s whereabouts in real time. That decision relied on the New Jersey Constitution, whereas the ruling Tuesday in the Fifth Circuit was made on the basis of the federal Constitution.
The Supreme Court has yet to weigh in on whether cellphone location data is protected by the Constitution. The case, which was initially brought in Texas, is not expected to go to the Supreme Court because it is “ex parte,” or filed by only one party — in this case, the government.
But the case could renew calls for the highest court to look at the issue, if another federal court rules differently on the same question. And two other federal cases involving this issue are pending.
“The opinion is clear that the government can access cell site records without Fourth Amendment oversight,” said Orin Kerr, a constitutional law scholar at George Washington University Law School who filed an amicus brief in the case.
For now, the ruling sets an important precedent: It allows law enforcement officials in the Fifth Circuit to chronicle the whereabouts of an American with a court order that falls short of a search warrant based on probable cause.
“This decision is a big deal,” said Catherine Crump, a lawyer with the American Civil Liberties Union. “It’s a big deal and a big blow to Americans’ privacy rights.”
The group reviewed records from more than 200 local police departments last year, concluding that the demand for cellphone location data had led some cellphone companies to develop “surveillance fees” to enable police to track suspects. [so the police are getting private businesses to monitor us to the 4th Amendment which forbids police spying without a warrant]
In reaching its decision on Tuesday, the federal appeals court went on to agree with the government’s contention that consumers knowingly give up their location information to the telecommunications carrier every time they make a call or send a text message on their cellphones.
“That means it is not protected by Fourth Amendment when the government goes to a third-party service provider and issues something that is not a warrant to demand production of those records,” said Mark Eckenwiler, a former Justice Department lawyer who worked on the case and is now with the Washington law firm Perkins Coie. “On this kind of historical cell site information, this is the first one to address the core constitutional question.”
Historical location data is crucial to law enforcement officials. Mr. Eckenwiler offered the example of drug investigations: A cellphone carrier can establish where a suspect met his supplier and how often he returned to a particular location. Likewise, location data can be vital in establishing people’s habits and preferences, including whether they worship at a church or mosque or whether they are present at a political protest, which is why, civil liberties advocates say, it should be accorded the highest privileges of privacy protection.
The decision could also bear implications for other government efforts to collect vast amounts of so-called metadata, under the argument that it constitutes “business records,” as in the National Security Agency’s collection of Verizon phone records for millions of Americans.
“It provides support for the government’s view that that procedure is constitutional, obtaining Verizon call records, because it holds that records are business records,” said Mr. Kerr, of George Washington University. “It doesn’t make it a slam dunk but it makes a good case for the government to argue that position.”
An important element in Tuesday’s ruling is the court’s presumption of what consumers should know about the way cellphone technology works. “A cell service subscriber, like a telephone user, understands that his cellphone must send a signal to a nearby cell tower in order to wirelessly connect his call,” the court ruled, going on to note that “contractual terms of service and providers’ privacy policies expressly state that a provider uses a subscriber’s location information to route his cellphone calls.”
In any event, the court added, the use of cellphones “is entirely voluntary.” [Yea, and so is going to the bathroom. But that doesn't mean the government has a God given right to listen to your cell phone call or watch you go to the bathroom]
The ruling also gave a nod to the way in which fast-moving technological advances have challenged age-old laws on privacy. Consumers today may want privacy over location records, the court acknowledged: “But the recourse for these desires is in the market or the political process: in demanding that service providers do away with such records (or anonymize them) or in lobbying elected representatives to enact statutory protections.” [I think what is happening here is the government is requiring private businesses to spy on us, and then saying it isn't a violation of the 4th Amendment because a private business is doing the spying, not the government.]
Cellphone privacy measures have been proposed in the Senate and House that would require law enforcement agents to obtain search warrants before prying open location records. Montana recently became the first state to require a warrant for location data. Maine soon followed. California passed a similar measure last year but Gov. Jerry Brown, a Democrat, vetoed it, saying it did not strike what he called the right balance between the demands of civil libertarians and the police.
Joanna Allhands thinks Tempe Town Toilet will be a disaster
Joanna Allhands thinks Tempe Town Toilet will continue to be a disaster for the taxpayers of Tempe????Also see:
Tempe Town ToiletSource
and
Tempe Cesspool for the Arts
Joanna Allhands | azcentral opinions
Posted on July 30, 2013 3:12 pm by Joanna Allhands
Incentives for Tempe Town Lake? Yeah, because that worked so well before
Truth: Tempe Town Lake development has never met its financial expectations. It doesn’t generate anywhere near the revenue necessary to cover the lake’s significant operational costs.
Truth: Over time, it’s smart to re-evaluate the city’s approach to speed lakeside development — even more so after a prolonged economic downturn. We must ensure that deals are fair to residents and enticing for businesses.
But is offering incentives the best way to do that? I’m skeptical, and Tempe residents should be, too. Let’s not forget:
– The previous City Council set a policy not to offer incentives unless they were for specific uses, such as historical preservation and environmental cleanup. That was under former Mayor Hugh Hallman, and I get that things are different now. But so different as to abandon that policy? I need convincing.
– Tempe has a poor track record of incentives and development deals, particularly when it comes to the lake. The city was embroiled in lawsuits and failed deals in the lake’s early days, which took years and cost millions of dollars to resolve. Do we really want to go down that road again, especially without specific performance expectations from businesses that receive the incentives?
Let me be clear: I was skeptical of plans city leaders floated to fund replacement Town Lake dams solely with land sales and private development. There just isn’t that much land left to produce the kind of cash we’re talking about.
But I’m equally skeptical of plans to have businesses pay less, if anything at all. Not so long ago, lakeside land at Mill Avenue and Rio Salado Parkway was named the Valley’s most desirable.
Has the market really changed so much that that’s no longer the case without giving businesses a financial break? Maybe. But I’d like proof.
Tempe OKs controversial lake plan
Tempe City Council sells out to special interest groups
All it takes is a few well placed bribes, oops, I mean campaign contributions and you can own you own Tempe City councilman or councilwoman.Well it's a little bit more complex then that. A $1,000 bribe, oops, I mean $1,000 campaign contribution to a Tempe City Councilman will get you $1 million in corporate welfare if you want to build something on the Tempe Town Toilet, which they call Tempe Town Lake. No I didn't document that, that's just my estimate of how corrupt the Tempe city government is.
The members of the Tempe City Council that sold us out to the developers are: Mark Mitchell [His daddy is former Tempe Mayor Harry Mitchell and Congressman Harry Mitchell, I think his brother is Robert Mitchell, a Tempe cop I sued in Federal court for false arrest and civil rights violations], Onnie Shekerjian, Robin Arredondo-Savage [yes I think she is related to convicted crooked Tempe City Councilman Ben Arredondo], Shana Ellis, Kolby Granville [he seems think he is the nut job neat freak Felix Unger of the Odd Couple and seems to be on a crusade to rid Tempe of messy yard criminals], Joel Navarro and Corey Woods
Tempe City Council sells out to rich developers of Tempe Town Toilet

|
||
|
Mayor Mark Mitchell
Son of former Tempe Mayor Harry Mitchell Brother of Tempe cop Robert Mitchell |
||

|

|

|
|
Onnie Shekerjian |
Shana Ellis |
Robin Arredondo Savage |

|

|

|
|
Kolby Granville |
Joel Navarro |
Corey Woods |
Tempe OKs controversial lake plan
By Dianna M. Náñez The Republic | azcentral.com Wed Jul 31, 2013 12:56 AM
The Tempe City Council voted Tuesday to revise the city’s Town Lake financing plan to offer greater incentives for developers. [translation bribes, oops, I mean campaign contributions in exchange for millions of dollars in corporate welfare]
The plan was unanimously approved despite a small window for public review and little opportunity for public comment on changes that would shift millions of dollars in lake costs to taxpayers. [That because the crooks on the Tempe City Council want as little media coverage of this theft as possible]
Early Tuesday, Tempe resident Ron Tapscott, a member of a city neighborhood association, sent Mayor Mark Mitchell and the council an e-mail pleading on behalf of taxpayers for a delay on the vote.
“I strongly encourage you to postpone a decision on this matter until it has been discussed and considered with community input,” Tapscott said.
Mitchell had earlier pushed to postpone a vote and allow input from taxpayers and businesses.
“This is something that’s important,” he said. “We’re going to have plenty of opportunity for (public) engagement.”
But Tuesday, Mitchell shifted his position and voted with the rest of the council to approve the changes.
The mayor asked Tempe Finance Manager Ken Jones to clarify the plan and note that it would not directly increase residents’ taxes nor delay improvements to community parks. [Those numbers are usually done using "politician math" which any 5th grader will tell you isn't the same math the rest of us use. "Politician math" can be call math that uses smoke, mirrors and lies to justify the users points]
Jones contended the developer incentives were “clarifications” to the lake finance plan. ["clarifications" my *ss, they are just more corporate welfare]
City finance officials have said the revised plan would give developers a financial break on their share of costs tied to the man-made lake and make private development more affordable. [That's government double talk that says the revised plan will make the TAXPAYERS pay the developers BILLS] The goal is to advance Tempe’s plans to secure sufficient lakeshore private development to ease the hefty public costs of maintaining Town Lake, finance officials said. [That's an oxymoron. Stealing money from the taxpayers and giving it to the developers isn't going to reduce the taxpayers costs. In fact it's going to increase the taxpayers costs. It's just smoke, mirrors and lies from the city of Tempe to cover up this outrageous corporate welfare]
While the plan was pushed as a solution to spur development that slowed as a result of the the Great Recession, the incentives for developers would come as the Tempe and national economy are improving.
Today, Tempe and state leaders were scheduled to attend a celebration in Tempe to mark the beginning of construction on Marina Heights, a $600 million project touted as the state’s largest office development.
Developers unveiled renderings of the 2 million-square-foot project that city leaders have boasted would drive Town Lake commercial and residential development.
Town Lake critics say that taxpayers have long carried the financial burden for private lake development, and the new plan offers no guarantee that economic breaks for developers would actually spur construction.
The revised plan would shift the burden of paying for a new west-end lake dam, which the city has estimated will cost at least $37.4 million, to Tempe taxpayers, freeing developers from sharing the expense of replacing the dam. [Again, when the damn was built the royal rulers of Tempe got screwed with a ORAL 30 year guarantee on the damn. When the damn failed 10 years after being built the guarantee was worth as much as the hot air that it was created with.]
Developers would pay a lower annual “holding fee,” which they typically begin paying when they build on their lake property.
The financing proposal also includes lowering the annual interest rate that developers must pay over the 25 years that they are allowed to pay back their share of lake construction.
Tapscott counted himself among the many Tempe residents who have endured community-service cuts. Under the revised lake-financing plan “substantial costs will be shifted to Tempe residents,” he wrote to council members.
Some Tempe residents have criticized the city for shifting millions of dollars to the Town Lake dam costs from spending that was approved by voters in a past bond election for community parks.
“The Alta Mira (Goodwin Park) neighborhood has diligently worked to improve our park, acknowledging the effects of a restricted city budget,” Tapscott wrote. “We sacrificed hours of master planning and hopeful expectation to accommodate the loss of city revenues from the economic recession.”
3 hops - A lame excuse to nullify the 4th Amendment
SourceWith 3 ‘hops,’ NSA gets millions of phone records
Associated Press Wed Jul 31, 2013 2:26 PM
WASHINGTON — President Barack Obama’s national security team acknowledged for the first time Wednesday that, when investigating one suspected terrorist, it can read and store the phone records of millions of Americans.
Since it was revealed recently that the National Security Agency puts the phone records of every American into a database, the Obama administration has assured the nation that such records are rarely searched and, when they are, officials target only suspected international terrorists. [Yea, sure!!!!]
But testimony before Congress on Wednesday showed how easy it is for Americans with no connection to terrorism to unwittingly have their calling patterns analyzed by the government.
It hinges on what’s known as “hop” or “chain” analysis. When the NSA identifies a suspect, it can look not just at his phone records, but also the records of everyone he calls, everyone who calls those people and everyone who calls those people.
If the average person called 40 unique people, three-hop analysis would allow the government to mine the records of 2.5 million Americans when investigating one suspected terrorist. [Give me a break. It would be IMPOSSIBLE for a small team of FBI cop to investigate 2.5 million Americans for every person they suspect is a terrorist. This 3 hop double talk is just a lame excuse to justify spying on millions of Americans]
The NSA has said it conducted 300 searches of its telephone database last year. Left unsaid until Wednesday was that three-hop analysis off those searches could mean scrutinizing the phone records of tens or even hundreds of millions of people.
“So what has been described as a discrete program, to go after people who would cause us harm, when you look at the reach of this program, it envelopes a substantial number of Americans,” said Sen. Dick Durbin, the No. 2 Democrat in the Senate.
John Inglis, the NSA’s deputy director, conceded the point but said NSA officials “try to be judicious” about conducting hop analysis.
“And so while, theoretically, 40 times 40 times 40 gets you to a large number, that’s not typically what takes place,” he said. “We have to compare the theory to the practice.” [So in reality the FBI doesn't investigate 2.5 million Americans for every suspected terrorists. But the FBI does want to use that lame 3 hop theory to give it an excuse to wire tape the phones of the 300+ millions Americans]
Such reassurances have done little to quell the sharp criticism from both parties over the once-secret program. Last week saw a close vote in the House on a measure that aimed to kill the phone surveillance program. [Yea, and they DIDN'T kill the program!!!]
On Wednesday, the administration acknowledged some limitations to its sweeping surveillance powers are inevitable.
“We are open to re-evaluating this program in ways that can perhaps provide greater confidence and public trust that this is in fact a program that achieves both privacy protections and national security,” Robert Litt, counsel to the Office of the Director of National Intelligence, told skeptical members of the Senate Judiciary Committee.
This newest privacy-vs.-security debate was touched off when former government contract systems analyst Edward Snowden leaked classified documents exposing National Security Agency programs that store years of phone records on every American. That revelation prompted the most significant reconsideration yet of the vast surveillance powers Congress granted the president after the Sept. 11, 2001, attacks.
The administration intended to keep the telephone program a secret, and for more than a decade few in Congress showed any interest in limiting the surveillance. Snowden’s leaks abruptly changed the calculus on Capitol Hill. [Snowden should be a national hero for exposing our corrupt government masters in the US House and Senate who have flushed the 4th Amendment down the toilet]
“We have a lot of good information out there that helps the American public understand these programs, but it all came out late,” Sen. Sheldon Whitehouse, D-Rhode Island, said in a rebuke of government secrecy. “It all came out in response to a leaker. There was no organized plan for how we rationally declassify this so that the American people can participate in the debate.” [Translation - we got caught flushing the Fourth Amendment down the toilet and I am trying to justify it with this double talk]
The telephone program is authorized under a provision of the USA Patriot Act, which Congress hurriedly passed after the Sept. 11,2001 attacks against the U.S. President George W. Bush’s administration said then what Obama’s administration says now: that in order to connect the dots, it needs to collect lots of dots. [Yea, using the unconstitutional Patriot Act which pretty much flushes the Bill of Rights down the toilet] Sen. Patrick Leahy was skeptical.
“There’s always going to be dots to collect, analyze and try to connect,” he said. “Government is already collecting data on millions of innocent Americans on a daily basis based on a secret legal interpretation of a statute that does not on its face appear to authorize this kind of bulk collection. So what’s going to be next? When is enough enough?” [The Patriot Act was enough. Congress should have repealed it, because it is unconstitutional. The courts should have struck it down because it is unconstitutional. I suspect the only way for it to end is an armed revolt by the people.]
Several Democrats promised bills that would provide tighter controls or more transparency. Proposals include eliminating the FBI’s ability to seize data without a court order, changing the way judges are appointed to the surveillance court and appointing an attorney to argue against the government in secret proceedings before that court. Another measure would force the government to reveal how many Americans have had their information swept up in surveillance. [All which is double talk and BS to justify the unconstitutional Patriot Act. The solution is simple - Repeal the Patriot Act!!!!]
Inglis said the NSA was willing to reconsider whether it needed to keep phone data for five years. And Deputy Attorney General James Cole said the Justice Department was considering whether and how to allow an outside attorney into the secret court to argue against the government. [Again the solution is simple - Repeal the unconstitutional Patriot Act!!!!]
Leaked docs give new insight into NSA’s searches
SourceLeaked docs give new insight into NSA’s searches
Associated Press Wed Jul 31, 2013 1:35 PM
LONDON — Documents published by the Guardian newspaper are providing new insight into the National Security Agency’s surveillance of world data, giving an over-the-shoulder look at the programs and techniques U.S. intelligence analysts use to exploit the hundreds of billions of records they gather each year.
Dozens of training slides published Wednesday divulge details about XKeyscore, one of a family of NSA programs that leaker Edward Snowden says has given America the ability to spy on “the vast majority of human communications.”
Some of the slides appear to carry screenshots showing what analysts would see as they trawled the intercepted conversations, including sample search queries such as “Show me all encrypted word documents from Iran” or “Show me all the word documents that reference Osama Bin Laden.”
In an indication of the program’s scope, one slide says that XKeyscore has led to the capture of more than 300 terrorists. In a statement, the NSA said that figure only included captures up to the year 2008, and pushed back against any suggestion of illegal or arbitrary collection of data.
“These types of programs allow us to collect the information that enables us to perform our missions successfully — to defend the nation and to protect U.S. and allied troops abroad,” the statement said.
How and from where the program draws its data isn’t completely clear, but one slide said XKeyscore was supported by 700 servers and 150 sites across the globe. Another slide seemed to show the program drawing data from a body codenamed SSO — an apparent reference to the NSA’s Special Source Operations, which previous Guardian articles have described as capturing large numbers of communications between the United States and other countries.
The volume of data available to analysts through XKeyscore appears to be vast. The Guardian quoted one slide as saying that nearly 42 billion records had been captured by the system during a one-month period in 2012 — a rate of half a trillion records every year. So much content was being collected, the newspaper said, that it could only be stored for short periods of time — generally just a few days.
“At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours,” the Guardian quoted one document as saying.
In a message forwarded to The Associated Press by Guardian spokesman Gennady Kolker, journalist Glenn Greenwald said the article about XKeyscore drew on half a dozen documents supplied to him by Snowden in Hong Kong. One of them — a 32-page overview of the program — was published in its entirety, albeit with several pages redacted.
The documents are the first to have been published in the Guardian since Snowden, who remains stuck at a Moscow airport, applied for temporary asylum in Russia on July 16.
Russian President Vladimir Putin said he’d be inclined to accept on condition that Snowden agreed not to hurt U.S. interests — implying that the American would have to stop leaking secrets. But Snowden’s Russian lawyer, Anatoly Kucherena, said Wednesday that the material for the article was provided long before Snowden promised to stop leaking.
“He warned me that he had already sent to the press an array of revealing information and secret documents and, unfortunately, could not stop its publication,” Kucherena was quoted as saying by the Interfax news agency.
Give Snowden his due: He made a surveillance debate possible
SourceGive Snowden his due: He made a surveillance debate possible
By Michael McGough
July 31, 2013, 12:42 p.m.
They call it the “Snowden effect.” Whatever you think of fugitive former National Security Agency consultant Edward J. Snowden -- hero, traitor, something in between -- his revelations about electronic surveillance programs have inspired a debate about broad questions of policy that was impossible because of the secrecy that enshrouded the programs themselves and their legal rationale. And that debate in turn has prompted defenders of the program to acknowledge that it can be reformed.
In Wednesday’s Washington Post, Sen. Dianne Feinstein, the chairwoman of the Intelligence Committee and a dogged defender of the NSA programs, says that she intends “to work with members of the Senate intelligence and judiciary committees to consider changes to the NSA call-records program in an effort to increase transparency and improve privacy protections.” That is the program under which the government collects so-called metadata -- information about the source, destination and duration of telephone calls.
Among other changes, Feinstein would have the government make public on an annual basis the number of Americans’ phone numbers “submitted as queries of the NSA database,” as well as the number of warrants obtained by the FBI to examine the actual content of phone calls. She also would reduce from five to two or three years the length of time phone records would be retained.
The improvements Feinstein proposes fall short of abolishing the bulk collection of telephone metadata unrelated to a specific terrorism investigation. But would even these refinements be on the table if Snowden hadn’t released information about the metadata program? Would President Obama be inviting congressional critics of the program (along with supporters) to the White House? According to Politico, the president will host a powwow on the surveillance program Thursday.
And without Snowden’s revelations, which continued Wednesday with a report in the Guardian about a versatile search program called XKeyscore, would the Senate Judiciary Committee be discussing changes in the way the secret Foreign Intelligence Surveillance Court operates and in how its judges are selected? Would the administration have released key documents about the metadata program, as it did Wednesday?
As they say in England, not bloody likely.
Even Obama, in the aftermath of the first Snowden leaks, said that he welcomed a debate over surveillance policy and whether it infringed on civil liberties. Without Snowden, that debate wouldn’t exist.
For that reason, some of Snowden’s supporters argue that he should be spared prosecution or even be given a presidential pardon. (Talk about “not bloody likely.”)
That doesn’t necessarily follow, for several reasons. Even if you don’t accept the notion that those who engage in civil disobedience should be willing to accept punishment, there is the question of whether some of Snowden’s leaks went beyond blowing the whistle on surveillance of Americans to compromise purely foreign intelligence.
But the “Snowden effect” is real, and salutary.
Too much information is being kept secret
'Classified' is government code for 'don't embarrass us'
I don't have a secret clearance and never have had one. But many times I have worked in secret engineering or manufacturing rooms, where I had to be baby sat by somebody with a secret clearance.All of the secret stuff I saw was down right ridiculous. A list of 50 resistors in a printed circuit board was classified. One board had an IC, that was secret before it was mounted on the printed circuit board, but once soldered on the printed circuit board was no longer secret.
When we moved a PC into a secret engineering room it literally took us 6 months to get an approval to do that from some secret bureaucrats in Washington D.C.
'Classified' is government code for 'don't embarrass us'
Our View: Too much information is being kept secret
By Editorial board The Republic | azcentral.com Wed Jul 31, 2013 5:49 PM
Army Pfc. Bradley Manning’s conviction is really the sideshow.
What deserves the spotlight is the creeping secrecy of government. Our government. The government that’s supposed to be a beacon of light and liberty.
More than 5 million government employees and contractors have security clearances. That’s a lot of secrets. A lot of secret-keepers. Too many.
The Government Accountability Office is looking at whether too many things are being classified and how the decisions are made to release information to the public.
Rep. Duncan Hunter requested the study. He told Foreign Policy that “classification inflation” limits public access to information that should be available.
In requesting the GAO study, Hunter pointed out another problem: “With access to classified information contingent on the issuance of security clearances, overclassification stands to dangerously expand access to material that should ordinarily be limited.”
Manning and Edward Snowden show the dangers of having too many secret-keepers.
It’s easy to find examples of overzealous classification.
One of the pieces of information Manning made public was a video of a 2007 U.S. helicopter attack in Iraq in which U.S. airmen laugh and call the targets “dead bastards.”
That attack killed civilians, including a Reuters news photographer and his driver. A subsequent military investigation showed the happy-go-lucky troops misidentified camera equipment for weapons before killing people they so callously denigrated.
The only reason for classifying that video is to protect the military from embarrassment — cover your backside.
What’s more, mixing in fake secrets with real ones increases the pressure to blow the whistle.
Manning says his motivation was to expose the military’s “bloodlust” and U.S. diplomatic deception. He dodged conviction on the most serious charge of aiding the enemy, but was convicted on 22 espionage, theft and other charges in the release of secrets to WikiLeaks.
As a soldier, he broke trust. But he did the public a favor. Whistle-blowing is a time-honored way to keep government accountable.
That’s especially true when the government is showing an adolescentlike fetish for hiding things that don’t need to be hidden.
Another example from very close to home:
The Department of Homeland Security refuses to make public what it knows about how many undocumented migrants get away, how many are caught multiple times or what percentage successfully enter the U.S. It’s classified.
The Arizona Republic sought the information. Now, Republican and Democratic members of Arizona’s delegation are asking for it, too. The lack of data makes it impossible to accurately assess the effectiveness of individual DHS border strategies.
If there’s a good national- security reason to hide information on border crossings, we haven’t heard it.
Snowden’s leaks about National Security Agency spying got him a one-way ticket to no man’s land. But it also put a light on the kind of government snooping that makes a lot of Americans queasy.
This nation is under threat from terrorists, and there are good reasons for keeping some information classified.
But Manning, Snowden and the DHS raise big concerns about what’s being withheld from the American people and why. That’s an issue that deserves the spotlight.
Russia grants NSA leaker Snowden asylum
Of course you have to remember that Russia is a police state just like the USA, and the Russian government is almost certainly doing this for political reasons. But even still Edward Snowden is a freedom fighter for exposing the corruption and law breaking by the US government.Russia grants NSA leaker Snowden asylum; he leaves airport
By Vladimir Isachenkov Associated Press Thu Aug 1, 2013 7:24 AM
MOSCOW — National Security Agency leaker Edward Snowden left the transit zone of a Moscow airport and entered Russia after authorities granted him asylum for one year, his lawyer said Thursday.
Anatoly Kucherena said that Snowden’s whereabouts will be kept secret for security reasons. The former NSA systems analyst was stuck at Moscow’s Sheremetyevo airport since his arrival from Hong Kong on June 23.
“He now is one of the most sought after men in the world,” Kucherena told reporters at the airport. “The issue of security is very important for him.”
The U.S. has demanded that Russia send Snowden home to face prosecution for espionage, but President Vladimir Putin dismissed the request.
Putin had said that Snowden could receive asylum in Russia on condition he stops leaking U.S. secrets. Kucherena has said Snowden accepted the condition.
The Guardian newspaper on Wednesday published a new report on U.S. intelligence-gathering based on information from Snowden, but Kucherena said the material was provided before Snowden promised to stop leaking.
Snowden, who revealed details of a U.S. intelligence program to monitor Internet activity, has received offers of asylum from Venezuela, Nicaragua and Bolivia and said he would like to visit those countries. However, the logistics of reaching any of those countries are complicated because his U.S. passport has been revoked.
Snowden’s father said in remarks broadcast Wednesday on Russian television that he would like to visit his son. Kucherena said he is arranging the trip.
The lawyer has said earlier that the temporary asylum would allow Snowden to travel freely around Russia, but wouldn’t allow him to leave the country. The one-year asylum can be extended.
WikiLeaks, a group which has adopted Snowden’s cause, said its legal adviser Sarah Harrison is now with him. The group also praised Russia for providing him shelter.
“We would like to thank the Russian people and all those others who have helped to protect Mr. Snowden,” WikiLeaks said on Twitter. “We have won the battle — now the war.”
Kucherena said that Snowden spent little time packing and left the airport in a taxi. The lawyer said the fugitive had friends in Russia, including some Americans, who could help ensure his security, but wouldn’t elaborate.
Snowden’s case has further strained U.S.-Russian ties already tense amid differences over Syria, U.S. criticism of Russia’s human rights record and other issues.
Putin’s foreign affairs aide, Yuri Ushakov, sought Thursday to downplay the impact this will have on the relations between the two countries.
“This issue isn’t significant enough to have an impact on political relations,” he said in remarks carried by Russian news agencies.
He said that the Kremlin hasn’t heard any signal from Washington that Obama could cancel his visit to Moscow ahead of next month’s G-20 summit in St.Petersburg.
Previous articles on the American War Machine.
More articles on the American War Machine.
 U.S. Rep. Kyrsten Sinema once toured Arizona on behalf of the White House, touting the benefits of health-care reform. Last week, the freshman Democrat voted with the GOP to delay the law’s requirement that individuals and businesses buy insurance by 2014.
U.S. Rep. Kyrsten Sinema once toured Arizona on behalf of the White House, touting the benefits of health-care reform. Last week, the freshman Democrat voted with the GOP to delay the law’s requirement that individuals and businesses buy insurance by 2014.